How to use Risk Cloud’s API to create or retrieve an API Access Token
The Risk Cloud API uses OAuth 2.0 for authentication, which uses a bearer token in the Authorization HTTP header. In order to start using the API, first retrieve your Client and Secret keys from the Profile page. This can be navigated to by clicking the Person icon in the top right corner and then the Profile button.
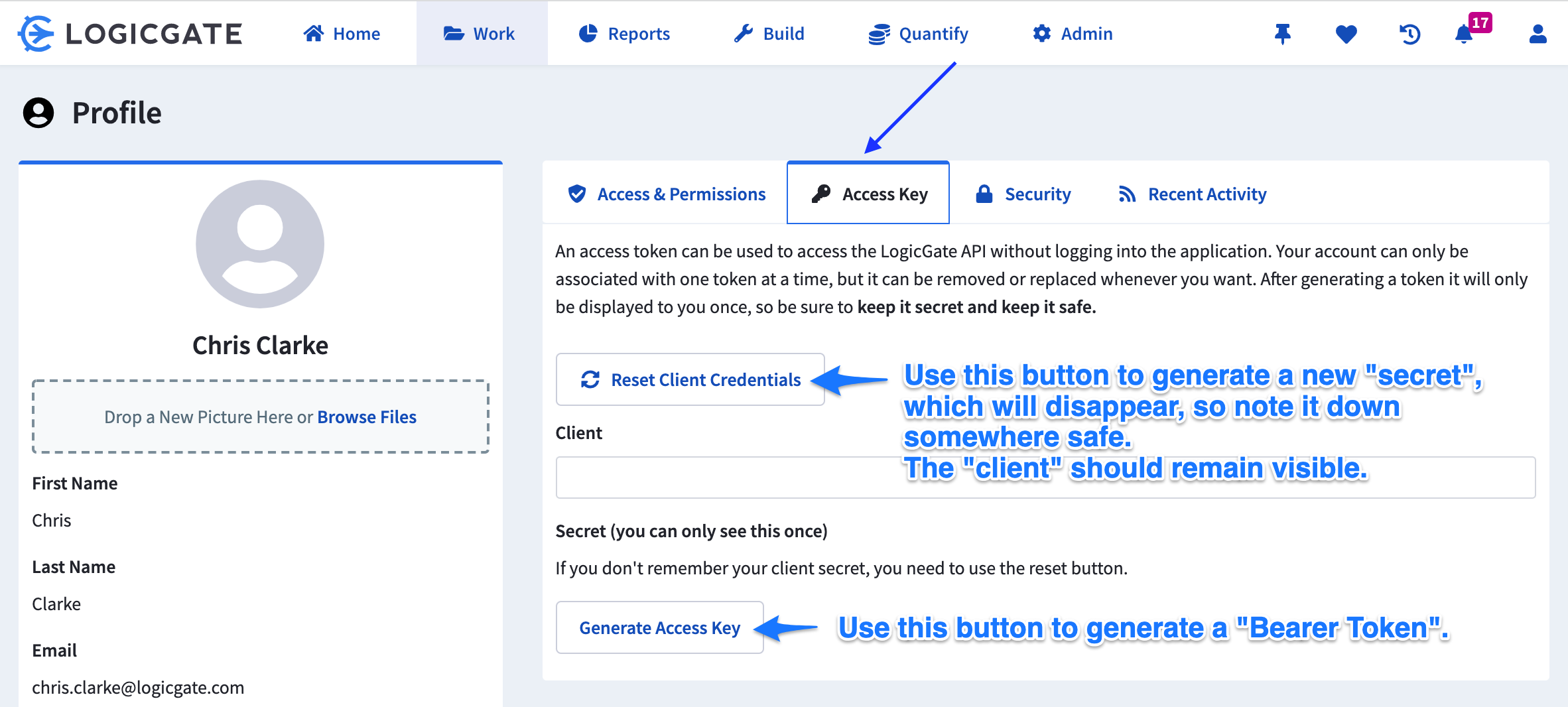
In the Profile page, go to the Access Key tab. If this tab is not there, please contact your Risk Cloud administrator as you may not have API privileges.
- In the Access Key tab, you will see both Client and Secret keys. These are both necessary to generate an access key or retrieve an existing access key.
- Use the Reset Client Credentials NOT the Generate Access Key button to generate a new secret. The client should stay visible.
- Note: This panel also has the ability to generate the Access Key aka the “Bearer Token” on its own.
After having both Client and Secret keys they will need to be base64 encoded.
- Encode via Terminal:
echo -n '{CLIENT}:{SECRET}' | base64 - Encode via PowerShell:
[Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes('{CLIENT}:{SECRET}'))
Once they are encoded, take your encoded string and place it in the authorization header as a “Basic Token” ex Authorization: Basic {ENCODED_BASE64_STRING}
Once this URL is pinged with the correct Authorization Header a JSON response will appear mimicking the following structure:
Response:
{
"access_token": "KEY_HERE",
"token_type": "bearer",
"expires_in": 31532918,
"scope": "read write"
}
The returned access_token can then be used in the authorization header as a “Bearer Token” to interact with Risk Cloud’s API
Authorization: Bearer {ACCESS_TOKEN}