Third-Party Risk Management: ISO 27001
Risk Cloud's Third-Party Risk Management: ISO 27001 Application is pre-built with a questionnaire aligned with ISO 27001's Annex…
Risk Cloud® is a no-code risk and compliance platform that scales and adapts to your changing business needs and regulatory requirements. It centralizes and connects all your risks, threats, controls, and evidence in one platform – so you can easily assess cyber risk and prioritize mitigation strategies.
The regulatory landscape is growing more complex every day, and the risks of being non-compliant are only increasing. To keep up, you need modern compliance control software that streamlines control evaluations and evidence requests.
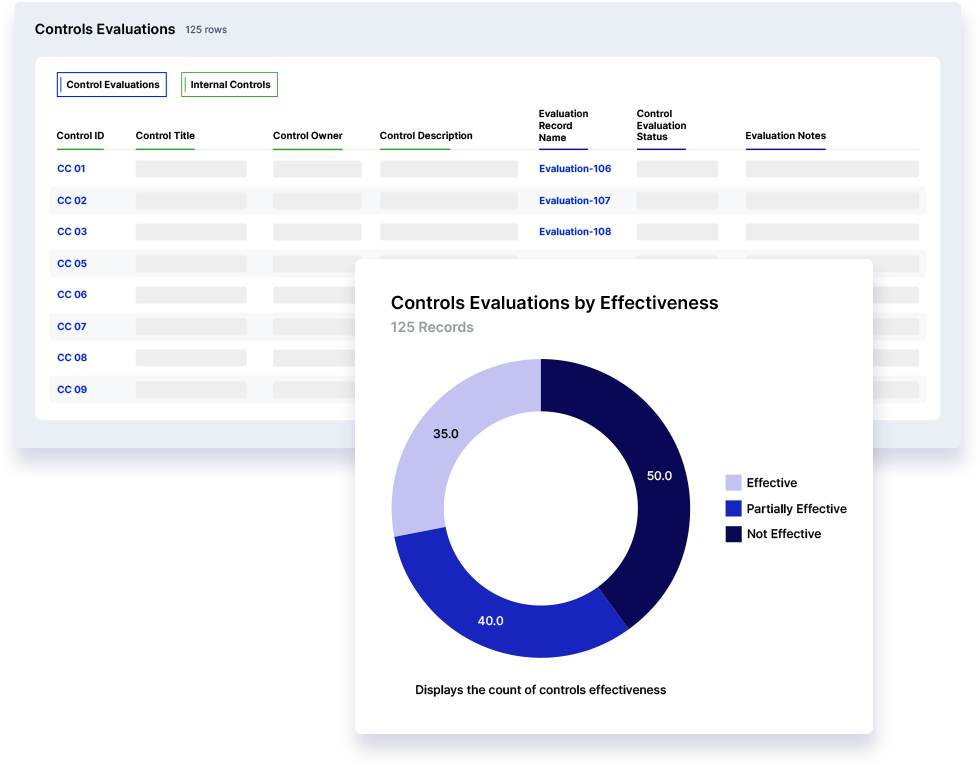
Risk Cloud’s Controls Compliance Application allows you to identify and document every control and test their effectiveness at scale.
Risk Cloud’s Controls Compliance Application aligns your audit assessments, requests, and tests with common control frameworks like HIPAA, ISO 27000, NIST CSF, SOC 2®, FFIEC CAT, and DSS. You’ll have everything you need to help you:
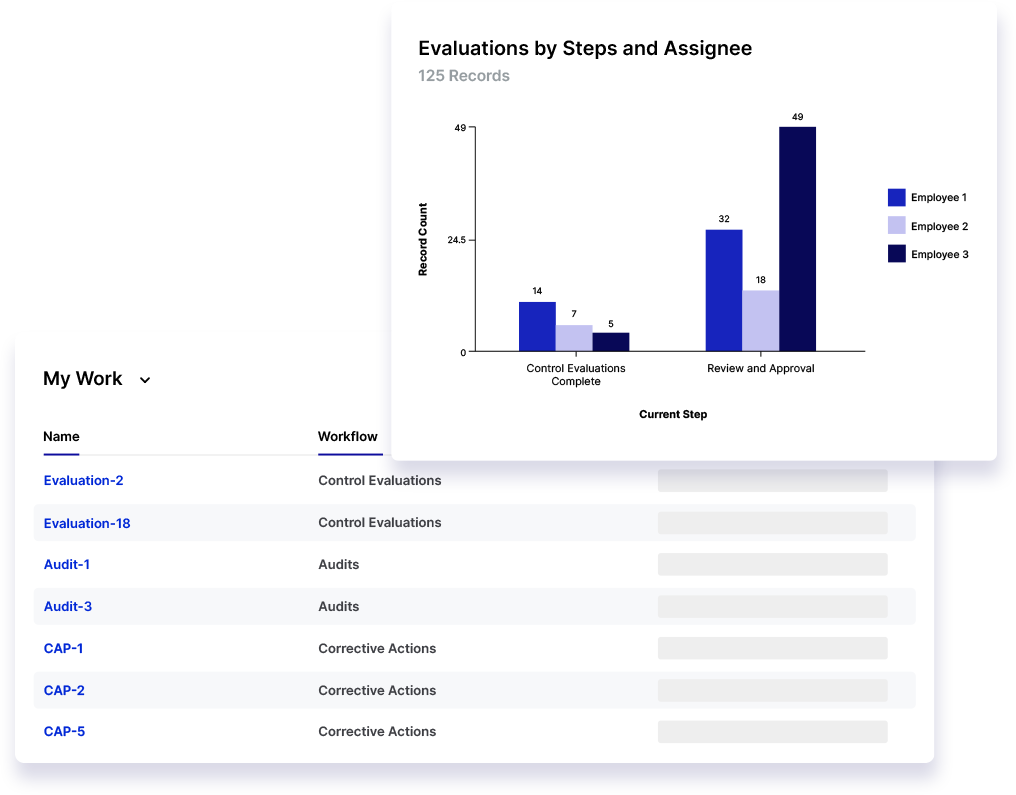
Risk Cloud centralizes compliance control evaluations, automates evidence collection, and streamlines reporting so you can uncover ineffective or broken controls in real-time and quickly take action to reduce risk exposure. Out-of-the-box integrations with leading communication tools like Jira and Slack further streamline workflows to help automate your team’s response.
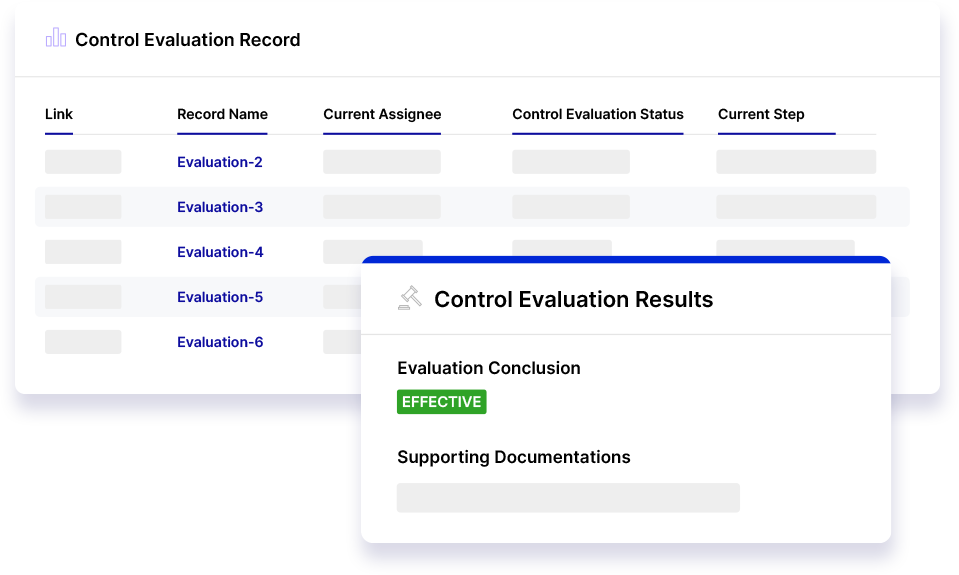
Evaluating control effectiveness, including scoring and evidence gathering, is time consuming. Risk Cloud provides pre-defined mappings between frameworks to eliminate duplicate assessments and automates control audits with out-of-the-box evidence collectors to give your team more time to analyze, share, and remediate findings.
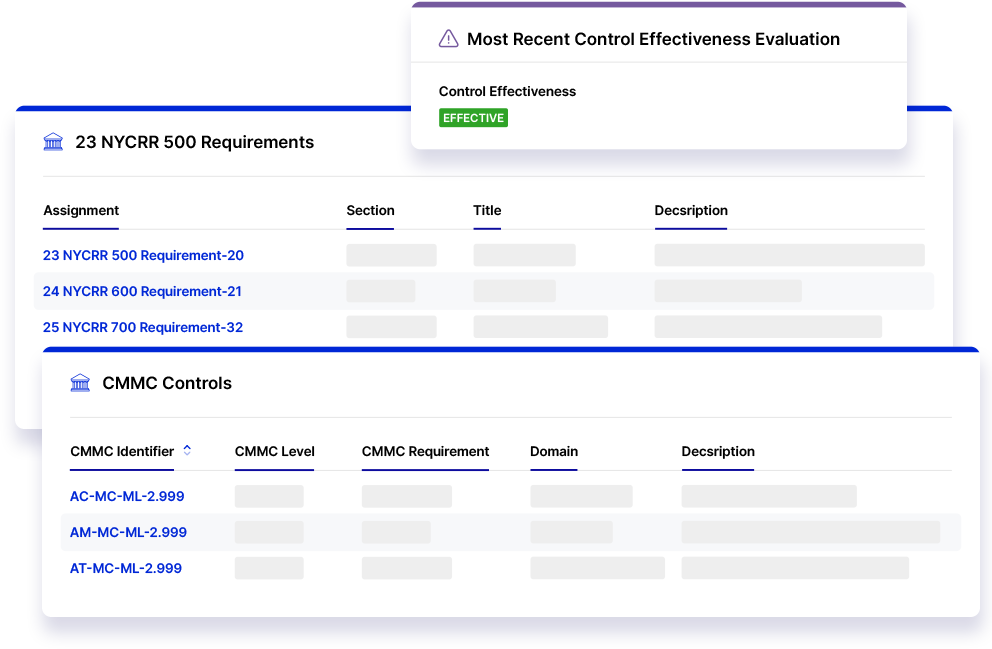
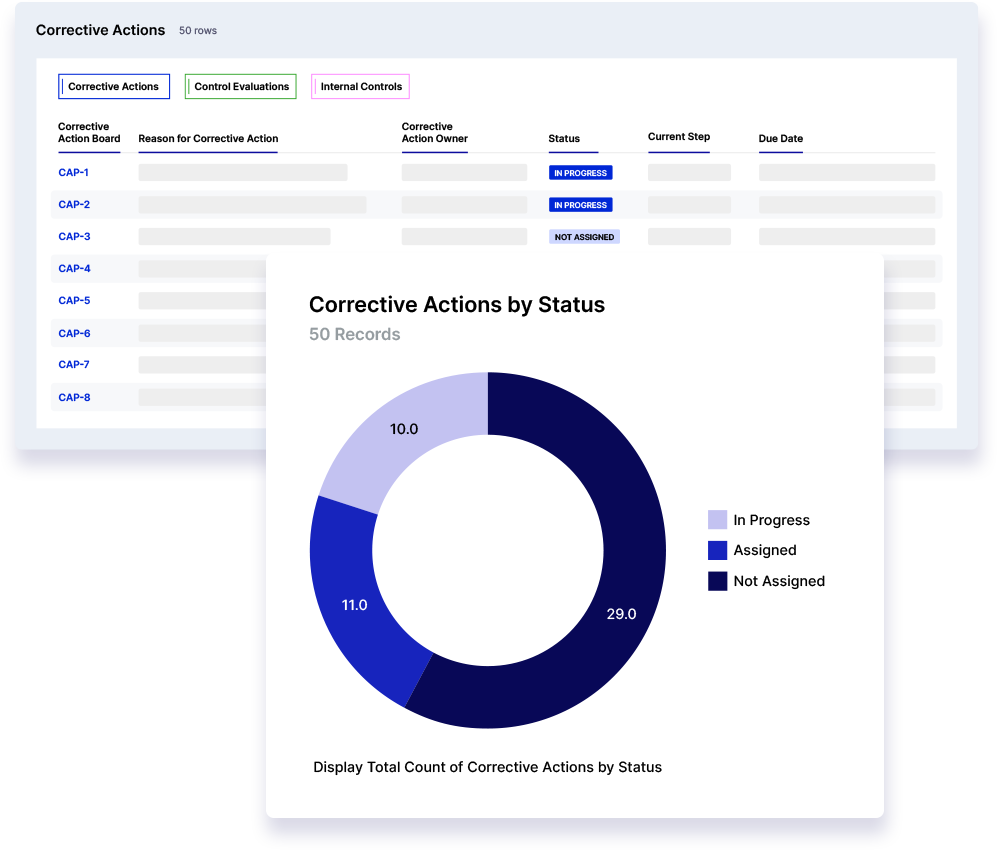
Initiate and assign corrective action plans when control gaps are identified. Track action plans through their resolution and generate reports to quickly visualize controls compliance and identify areas for improvement.
SOC 1®, SOC 2® and SOC 3® are registered trademarks of the American Institute of Certified Public Accountants in the United States. The AICPA® Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy is copyrighted by the Association of International Certified Professional Accountants. All rights reserved.
Risk Cloud's Third-Party Risk Management: ISO 27001 Application is pre-built with a questionnaire aligned with ISO 27001's Annex…
Vulnerability Management Application helps organizations manage and assess the vulnerability impact.
Risk Cloud’s Enterprise Risk Management Application makes it easy to build your holistic risk management process as it…
