Business Impact Analysis: NIST 800-34
Risk Cloud’s Business Impact Analysis: NIST 800-34 Application helps organizations identify outage impacts, estimated downtime, resource requirements, and…
Risk Cloud® is a no-code risk and compliance platform that scales and adapts to your changing business needs and regulatory requirements. It centralizes and connects all your assets, vulnerabilities, and treatment plans in one platform – so you can easily assess cyber risk and prioritize mitigation strategies.
Avoid downtime and protect critical assets with automated vulnerability impact assessments and mitigation plans. Risk Cloud’s Vulnerability Management Application provides a single source of truth and automated workflows for logging, analyzing, and treating vulnerabilities to help your teams quickly act to minimize their business impact.
Gain the clarity you need to prioritize treatment plans and minimize risk at your organization by leveraging Risk Cloud as a single source of truth for asset, vulnerability, and mitigation tracking. The Vulnerability Management Application includes pre-built, configurable workflows to help you:
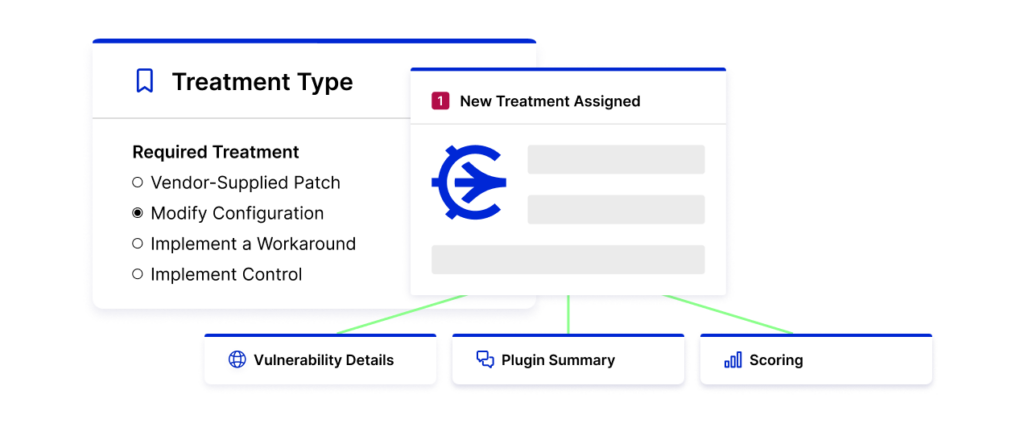
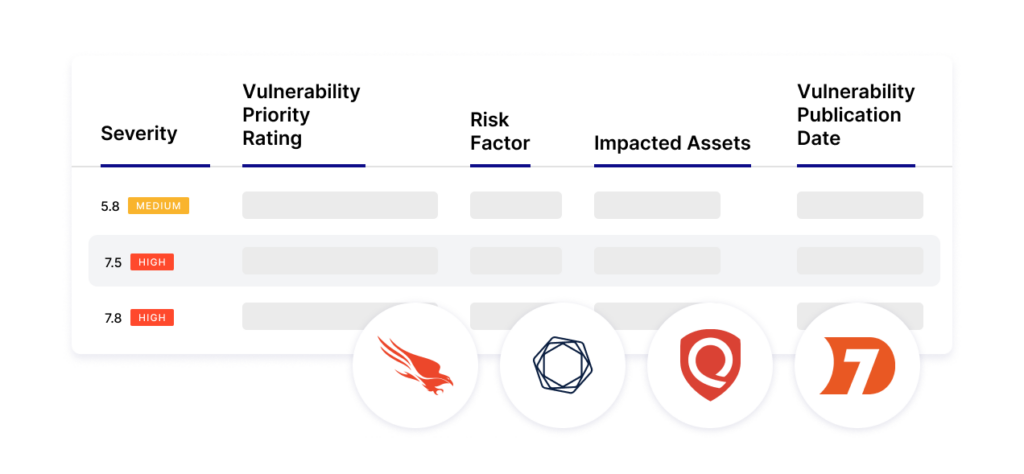
Stay ahead of the latest threats by automatically pulling vulnerability information like description, severity, affected assets, and recommended remediations into Risk Cloud from vulnerability management tools like Tenable.io, Qualys, CrowdStrike, and Rapid7. Centralize assets, related vulnerabilities, assessment activities, and treatment plans for near real-time visibility into inherent and residual risk at your organization.
Notify teams about critical vulnerabilities as they are discovered, then immediately assess related business impact and assign treatment plans with automated workflows in Risk Cloud. Simplify the review process and accelerate remediation by viewing all relevant vulnerability information in a single click. Keep teams on track with assignment notifications and reminders in the tools they use every day, like Slack, Jira, and Microsoft Teams.

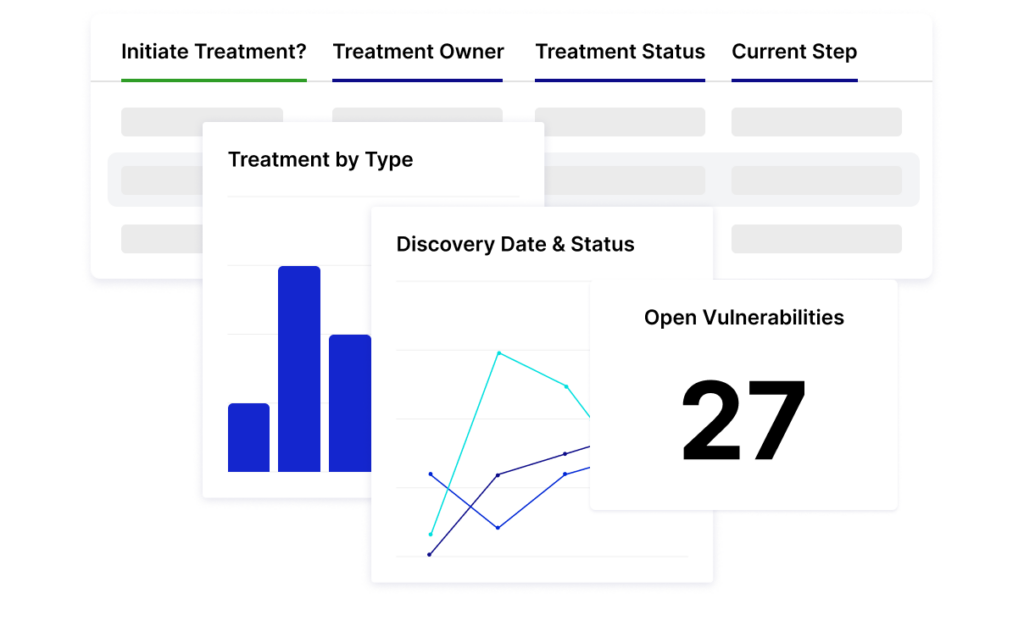
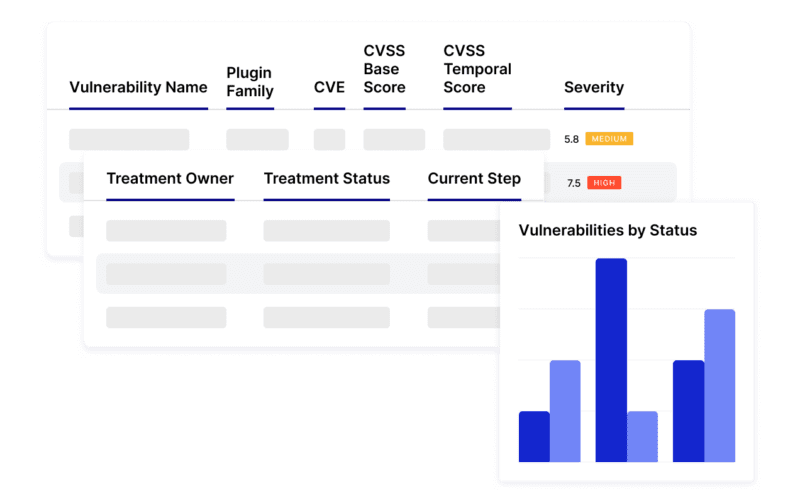
Centralize and transform data into meaningful insights with Risk Cloud’s out-of-the-box reports that can be configured to your unique needs. Visualize key program insights like count of open vulnerabilities, open vulnerabilities by severity, treatment status, and number of vulnerabilities fixed over time. Streamline communication to stakeholders with role-based dashboards that only show the most relevant information to each audience.
Risk Cloud’s Business Impact Analysis: NIST 800-34 Application helps organizations identify outage impacts, estimated downtime, resource requirements, and…
Risk Cloud’s Cyber Risk Management Application unlocks a connected view of assets, threats, and vulnerabilities so you can…
Risk Cloud’s Controls Application assists organizations in assessing, evaluating, and remediating controls in-scope for the organization, all within…
