Software
You need fast and agile risk management, we’ve got you.

We are driven to provide the best possible security and offer our future and current customers insight into our security strategies and tactics. We strive to create a dialogue that highlights our respective roles in our relationship with our customers, offer transparency, and ultimately help make all of us more secure.
We design our systems to treat all customer data as critical, with key data protections around all of the data you choose to upload into Risk Cloud. These data protections include but are not limited to:
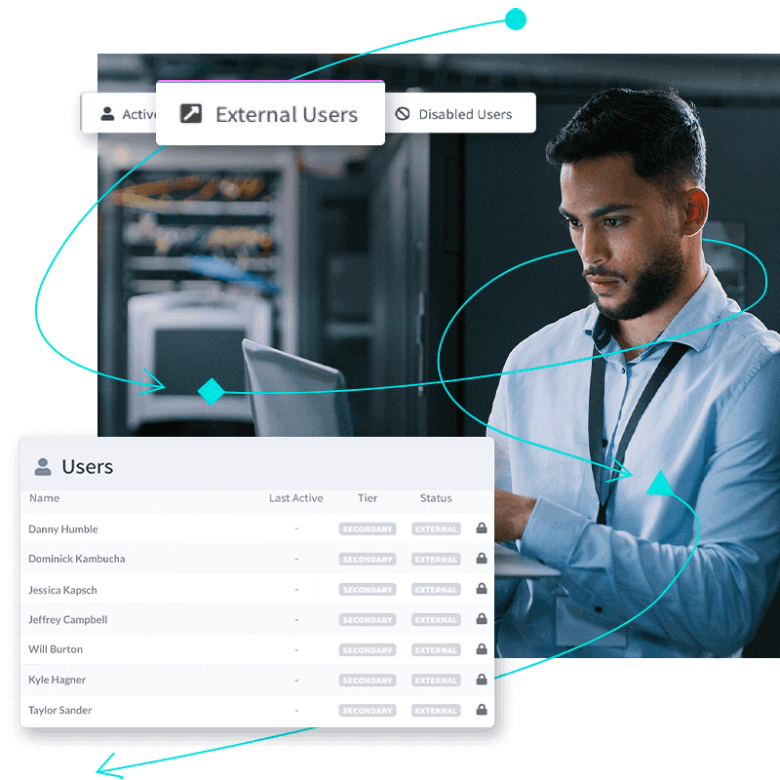
LogicGate’s Risk Cloud platform is monitored for operational performance, availability, and security events. Examples of the types of security events include abnormal external network interactions, platform behavior abnormalities, and internal user behavior changes. Our InfoSec and DevOps teams employ a security information and event monitoring (SIEM) platform to help ensure that there are no security ramifications based on any alerts we receive.
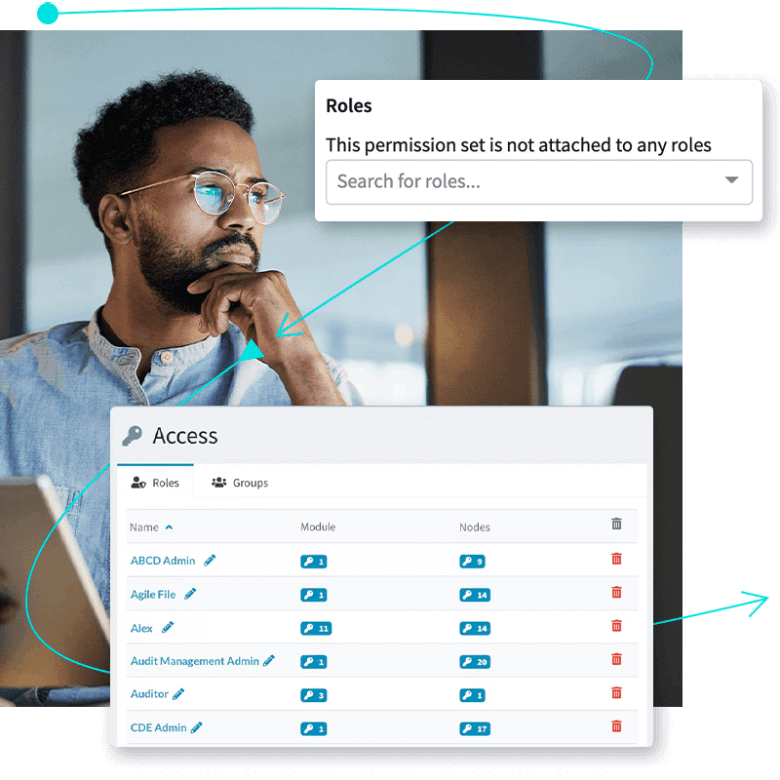
If a suspected incident is identified, our incident response team has an established plan to investigate and address the situation. Key aspects of our incident response plan include:
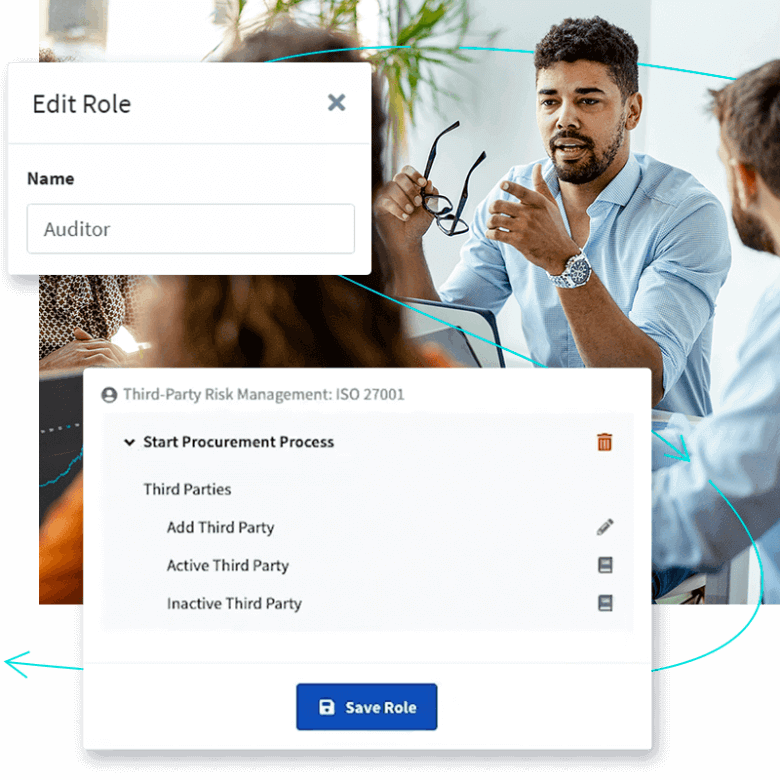
We understand that the threat landscape is constantly evolving. To ensure that we are evaluating these ever-changing threats, we have established the following methods to identify and remediate risks in our platform:
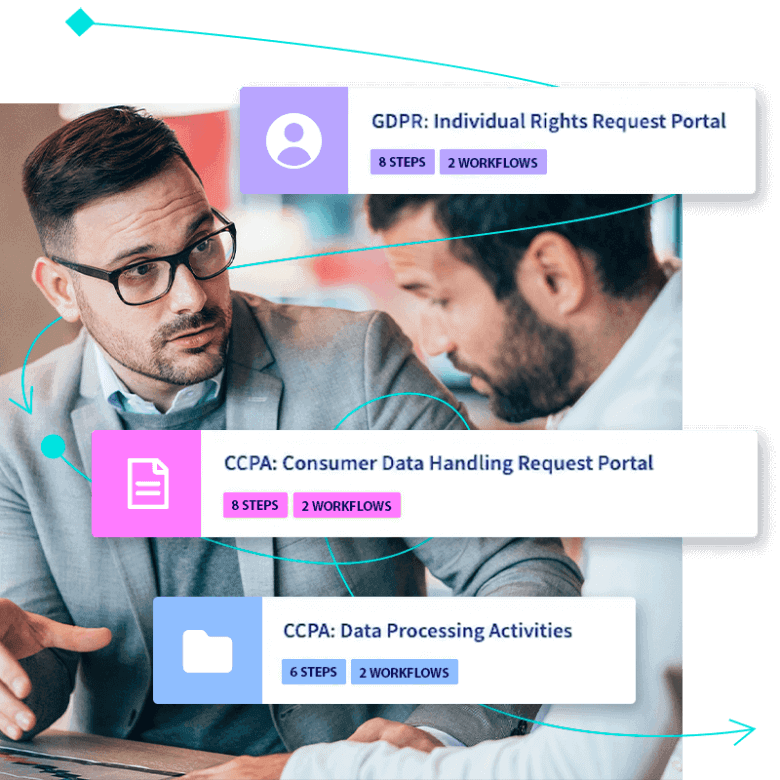
LogicGate seeks to align our security controls with our various privacy and compliance requirements to ensure you can effectively manage your data and implement controls to meet your compliance needs.
Additionally, we are a chief user of our platform, leveraging it to drive our operational processes and meet our compliance and certification goals.
You need fast and agile risk management, we’ve got you.
Scale compliance processes while scaling your business. Check and check
Modern healthcare compliance can be challenging. But not with Risk Cloud.
Centralize your audit, risk, and compliance solutions so you’re ready for just about everything.
We’ll connect your GRC processes while you connect the world.
The toughest quality control standards are no match for you with Risk Cloud’s ERM solutions.
With Risk Cloud, you can navigate risk and uncertainty with confidence.
A platform that helps you define, score, and monitor risk across your org? Score!
Make every day an incident-free day with protocols fueled by smarter tech.
Cut out risks to keep the lights on. Power your GRC processes with Risk Cloud.
Struggling to meet constantly changing standards? Maybe it’s time to try an alternative solution.
Remain compliant in today's complex regulatory environment.
