A cyberattack is stifled before it affects a single one of your servers. You’ve got loads of cash reserves to weather the economic downturn. Supply chain problems? You’ve got back-up suppliers lined up six ways from Sunday. The walls of your organization are a risk-proof fortress.
But risk doesn’t stop at your office walls or your firewalls. Risk leaders need to consider all of the things that could go wrong inside their organization as well. Managing this type of risk is known as operational risk management.
Standing up an operational risk management program is similar in many ways to building strategic or enterprise risk programs, but it also differs in many ways. This article will dive into what types of operational risk organizations face and how to identify, measure, and mitigate the ones threatening your own business.
What is operational risk?
Operational risk is defined under Basel II as the risk of loss resulting from ineffective or failed internal processes, people, systems, or external events that disrupt normal business operations. In short, it’s the risk that an employee will make a mistake, a process will fail to achieve its purpose, or a system will break down or become compromised, leading to a risk event.
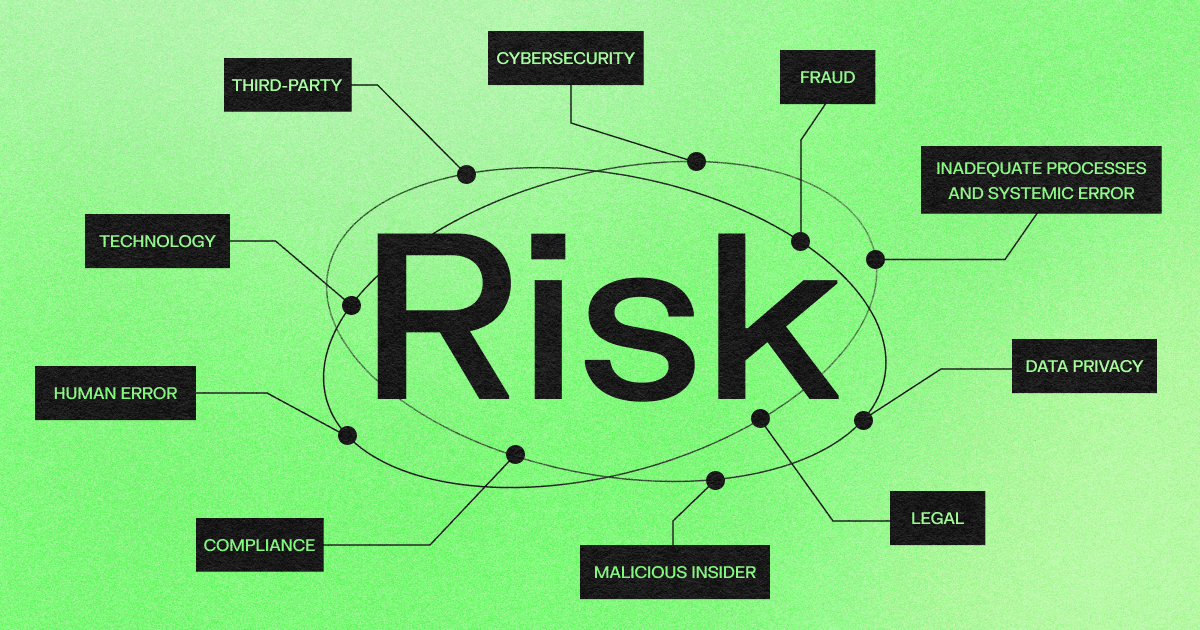
Here are a few examples of what operational risk from each category might look like:
People
Operational risks originating with people can result from inadequate staffing levels leading to important tasks being overlooked and shortcuts being taken, policies being misunderstood or ignored, malicious insider activity, or ineffective workforce training.
Processes
The more complex your internal processes are, the higher the chance one or more crucial steps in the process will get missed and operations will become broken, delayed, inefficient, or more costly.
Systems
Cybercrime and other cyber threats are on the rise, and falling victim to one can lead to damaging data breaches or, worse, cripple your organization. Failing to properly secure your systems and take measures to detect and ward off bad cyber actors can expose your organization to operational risk.
External events
This type of operational risk came into full focus when the COVID-19 pandemic essentially shut down the global economy—and the supply chains that power it—for the better part of two years. Any events that interrupt your business’s operations, from a change in local political leadership to an earthquake or hurricane, is an operational risk originating outside your organization. These risks can also fall under the category of enterprise risks.
How can operational risk affect your organization?
Every company faces operational risk every day just by virtue of doing business. As operations become more complex, it becomes increasingly likely that things will fall through the cracks, policies will collect dust on a shelf or fail to be communicated as the workforce grows, or controls that haven’t been continuously monitored and updated will begin to fail.
All of this increases exposure to operational risk over time, making it more likely that one will materialize and impact your revenue or brand reputation.
Types of operational risks
Organizational risk can come in a variety of forms and many are unique to the specific industry your organization is operating in, but here are some of the most common types of organizational risk you can expect to face.
Compliance risks
Compliance risk is the risk that your organization will fail to stay compliant with regulatory requirements, raising the likelihood that you’ll be subject to negative audit findings, fines, and other penalties.
Third-party risks
Every third-party service provider or vendor you work with represents another vector for operational risk to enter your organization. Plus, the third parties you work with almost certainly do business with a network of third parties themselves, introducing the potential for this type of risk to grow exponentially. Each must be vetted to the fullest extent to ensure none of that third-party risk makes it through your business’s front—or back—door.
Cybersecurity risks
As digital tools and cloud-based services proliferate and work is increasingly performed over the internet, organizations have begun to face more frequent and more sophisticated cyber attacks. Every connection point to your organization’s network—every laptop, smartphone, or even printer—is a potential spot for bad actors to squirm in and cause headaches or worse.
Technology risks
Another source of operational risk in the vein of cybersecurity risk is technological risk. This is the risk that your technology will stop working properly and slow or halt operations, cause significant downtime, and lead to other negative outcomes. This type of risk is especially important to be paying attention to as the majority of organizations accelerate their digital transformations.
Data privacy risks
Significant portions of daily life are being conducted over the internet these days, and each task completed, item purchased, form submitted, and video watched creates data. Some of this data—lots of it, in fact—can be of a very personal nature, and it’s critical that organizations keep this information secure. Failing to do so can cause irreparable harm to your customers, draw the ire of regulators, and lead to significant financial and reputational damage.
Human error risks
Everyone makes mistakes from time to time. But a lot of the errors that have the potential to derail your operations in some way can be prevented by proper operational risk management practices and effective employee training programs. These include data entry error, failing to follow processes properly, inadvertent release of sensitive information, and other mistakes.
Malicious insider and fraud risks
Unfortunately, employee actions that cause problems for your business aren’t always inadvertent. Disgruntled employees, corporate thieves, saboteurs, and other bad actors in your midst all raise your business’s risk of experiencing a malicious insider attack.
Occupational safety risk
Any job your employees work on can expose them to different kinds of occupational safety hazards, whether they’re hauling bags of concrete to a construction site or programming source code for a digital product at their desk. These hazards can affect both physical and mental health, and they can happen entirely by accident, or because someone ignored safety protocols.
Legal risk
Any of the operational risks we covered above can expose your business to legal risk, too.
Operational risk examples
Let’s take a look at operational risk in the wild with real-world examples from some of the world’s most recognizable brands and institutions, and some associated with emerging technologies:
- Vendor risk—Target: Target was famously hacked when cybercriminals were able to access their networks by compromising computers used by a third party contractor working on the chain’s HVAC systems. The bad actors stole the HVAC company’s credentials, then used them to exfiltrate reams of customer data.
- Technology and human error risk—Citibank: Citibank lost millions when it accidentally paid off a $900 million loan for cosmetics giant Revlon due to a confusing interface in the financial software it was using. Courts later ruled that Revlon and its creditors didn’t have to pay the money back.
- Technology risk—generative artificial intelligence: Emerging technologies like ChatGPT and other generative AIs could eventually supplant, partially or in whole, software tools used to complete common tasks. This could pose an existential threat to businesses building those tools.
- Compliance risk—Binance and Coinbase: Cryptocurrency exchanges Coinbase and Binance will both shell out expected millions after regulators alleged they violated various anti-money laundering, corruption, and bribery laws.
- Occupational safety risk—National Football League (NFL): After numerous current and former professional football players alleged that they had suffered severe traumatic brain injury due to hits taken during their careers, the NFL agreed to pay hundreds of millions in compensation.
- Data privacy/cybersecurity risk—T-Mobile: Telecomm giant T-Mobile is on the hook for $500 million after a data breach compromised personal information on 76.6 million people.
What is operational risk management?
The natural response to operational risk of any kind is to find ways to manage it. That’s where operational risk management enters the picture. Operational risk management is a subdiscipline of enterprise risk management that provides for processes for identifying, measuring, reporting, managing, and mitigating operational risk.
What is the goal of operational risk management?
The end goal of any operational risk management program is to anticipate and prevent as many operational risks from materializing and causing problems for an organization as possible. Companies that experience fewer operational risk events will be more trusted by their customers and clients, and that improves investor confidence, brand reputation, and the overall bottom line.
Operational risk management vs. strategic risk management
While operational risk can stem from strategic risks and errors associated with them, the two are distinct concepts. As defined above, operational risks come into play when processes fail, policies are ignored, systems break down, and other events that interrupt the flow of business occur.
Strategic risks, on the other hand, are related to the overall planning, management, and strategy of the business. These are things like not having clear goals or priorities, departmental siloing or tribalism, turbulence and inconsistency caused by turnover in management, competitors eating into revenue, a poorly executed merger and acquisition, or the introduction of a new product that flopped.
Operational risk management also puts a much heavier emphasis on protecting the organization from risks that could cause problems, while part of strategic risk management is looking for the right risks that can be taken, rather than avoided, to generate strategic and competitive advantages.
The four principles of operational risk management
Few organizations deal with higher-stakes risk scenarios than the U.S. military. Naturally, they put extensive time and resources into developing operational risk management programs and training personnel on adhering to them. The U.S. Navy has developed four specific principles that underpin their operational risk management process:
- Accept risks when the benefits outweigh the cost: Sometimes, risks simply need to be taken to make meaningful progress toward a specific goal. As the famous mantra goes: “no risk, no reward.” When the potential benefits of accepting a particular risk are clearly much higher than the potential loss of doing so, or when there’s no other way to achieve the objective without taking that risk, then it makes sense to do so. Ensure any plan of action is approved through the appropriate channels first.
- Accept no unnecessary risks: On the other end of the spectrum, you shouldn’t get into the habit of accepting operational risks for lack of effort put into mitigating them or if the benefits are negligible at best or unlikely to materialize.
- Anticipate and manage risk by planning: There’s no worse way to manage risk than by flying in blind. That’s why it’s important to take the time to develop business continuity plans and put controls in place to mitigate operational risks.
- Make risk decisions at the appropriate level: Organizations are more agile and more likely to catch and prevent risks from materializing early when everyone is empowered to carry out operational risk management. That said, it’s critical that the organization’s party line for what constitutes an acceptable risk and what does not.
Establishing effective frameworks and policies for managing operational risk
Now that we have a deeper understanding of what operational risk and operational risk management are, let’s get into how to build a program for managing operational risk. We’ll cover the basics of taking stock of all your organization’s operational risks and carrying out an operational risk assessment, plus more advanced techniques like using key risk indicators and risk quantification to stay on top of them.
Identify your operational risk
It’s impossible to start effectively managing operational risk without knowing which operational risks you’re facing. That’s why the first step in standing up any solid operational risk management program is to get a clear view of your organization’s entire risk landscape.
Assess, quantify, and prioritize your operational risk
Then, you can begin to prioritize which operational risks pose the gravest threat to your business. The best way to do this is to use risk quantification and risk scoring methods, like Monte Carlo simulations and the Open FAIR framework to tie each risk to its potential financial impact.
Develop a plan to mitigate operational risk
With your prioritized list of risks in hand, you can now begin taking steps to mitigate operational risk in a variety of ways.
- Transferring risk: There are a few ways you can go about transferring risk, but the most common way is insuring against your risk. We’re seeing a lot of this in the cybersecurity industry right now, where many organizations are purchasing cyber insurance to help absorb the costs of data breaches or other cyber incidents.
- Avoiding risks: The surest way to make sure an operational risk doesn’t cause problems for your business is to avoid the risk altogether. But this comes with a trade-off: It might require you to bow out of a market, industry, or product that it would be impossible to build or operate in without dealing with that risk.
- Accepting risks: On the other hand, you could accept the risk. Remember, one of the four principles of operational risk management is to “accept risks when the benefits outweigh the costs.” If there’s a lot of upside to embracing a particular risk and little downside, go for it. Just do your diligence to ensure that the little downside is, indeed, little.
- Implementing controls: This is the middle ground between avoiding and accepting risk, and it’s the most common method of managing operational risk at most organizations. Putting controls in place to mitigate risk allows organizations to operate with the risk present, but ensure there are guardrails to keep it from becoming a problem. If you’re concerned about theft of IP or merchandise, putting security cameras and better locks on your office’s entrances and exits would be an example of implementing a control. If you’re concerned about cyberattacks (as we all should be these days), then adopting zero-trust practices could be an effective control to prevent them.
Once you’ve finished assessing each operational risk and developing your mitigation plans, ensure that the plans, policies, and protocols that emerge from the process are clearly communicated out into the rest of your organization.
Continuously monitor operational risk
One constant in the world of operational risk management is change, and that’s why you need to always be measuring, monitoring, and adjusting your controls and plans. The plans you developed in the previous steps should also include a regular cadence where your team evaluates each of your controls and improves them where necessary.
An effective way for conducting continuous controls monitoring is by developing a good set of key risk indicators. More on that below.
How to set KRIs for measuring operational risk
Key risk indicators, or KRIs, are metrics designed to warn you of impending risk events or trends that could lead to risk events. They estimate the overall likelihood that the risk being monitored will occur, how fast that could happen, and the potential impact if it does occur.
You can assign KRIs to each of your operational risks as follows:
- For each operational risk in your risk register, work backwards from the event to identify the root causes, i.e. everything that would need to happen, in the order they’d need to happen, for that risk to materialize.
- Identify sources of data that can be used to measure the number of occurrences of each of those events or how likely they are to happen. For customer churn, data from your CRM or net promoter score could be used for this, while cybersecurity KRIs tracking phishing could rely on the number of simulated attempts passed and failed.
- Create dashboards using modern GRC software to obtain an eagle-eye view of the trends that your KRIs are tracking.
Common challenges and mistakes in operational risk management
As with any aspect of risk management, operational risk management comes with its own set of challenges and pitfalls that can derail your well-laid plans or even open your organization up to additional risk exposure. Here are a few of the common challenges and mistakes made in operational risk management.
- Relying on manual processes and workflows: Any time one of the processes you rely on to manage your operational risk relies on manual execution, there’s the potential for human error (meta: that’s an operational risk!) to introduce inconsistency, and doing things manually is inefficient and expensive.
- Solution: Automate your operational risk management program with modern GRC technology.
- Siloing of risk data: Operational risk affects your entire organization, and all of the data you have available to track and manage is essentially useless if it never leaves the department it originated from so that everyone in the organization can have eyes on it. Risk management is a team sport.
- Solution: Use modern GRC technology to centralize your risk data, so everyone is on the same page about how operational risk should be handled.
- Difficulty getting executive buy-in for initiatives: It’s tough to get leadership to support your operational risk management initiatives if you don’t have an effective way of communicating the consequences of neglecting operational risk and the benefits of properly managing it.
- Solution: Modern GRC technology can help you report the right information to the right people, at the right time, to build support for your programs.
- Difficulty scaling operational risk programs as organizations grow: As an organization grows, its operations, risk landscape, and controls become more and more complex. Scaling an operational risk management program becomes very challenging under these circumstances.
- Solution: Modern GRC technology can help you automate, scale, and connect your risk program as your organization grows. Platforms built on graph databases, like LogicGate Risk Cloud, are flexible enough to be changed on the fly and evolve with your growing initiatives.
Fortify your operational risk strategy
There’s no avoiding it: If you’re operating a business or any other type of organization, you’re going to have to deal with operational risk. Standing up an effective operational risk management program is the best way to get ahead of—and stay ahead of—any risk facing your business.
Click here to learn how LogicGate Risk Cloud can help you fortify your own operational risk program.