Over the past year, as healthcare organizations were focused on tending to the COVID-19 pandemic, ransomware attacks were relentless in targeting this industry. However, the healthcare sector wasn’t the only group targeted, organizations across all sectors continue to be targeted by ransomware attacks. The top three methods of entry for these attacks—email phishing, Remote Desktop Protocol (RDP), and software vulnerabilities—are largely preventable, but there is no single solution to solve this problem. In order to combat ransomware, your organization needs to approach the problem holistically to include using specific threat scenarios (actors/tactics/techniques) to fine-tune how you evaluate and treat vulnerabilities.
Many organizations perform some form of vulnerability scanning within your environments today. However, performing scans is only part of a truly holistic approach to vulnerability management. Failing to execute other more holistic functions is what can lead to gaps in securing organizations against dynamic threats like ransomware. A robust approach should include elements such as Asset Awareness, Vulnerability Governance, various forms of Testing/Assessments (not just vulnerability scans), ties to Risk Management, and a robust Change Management capability as illustrated in the diagram shown below.
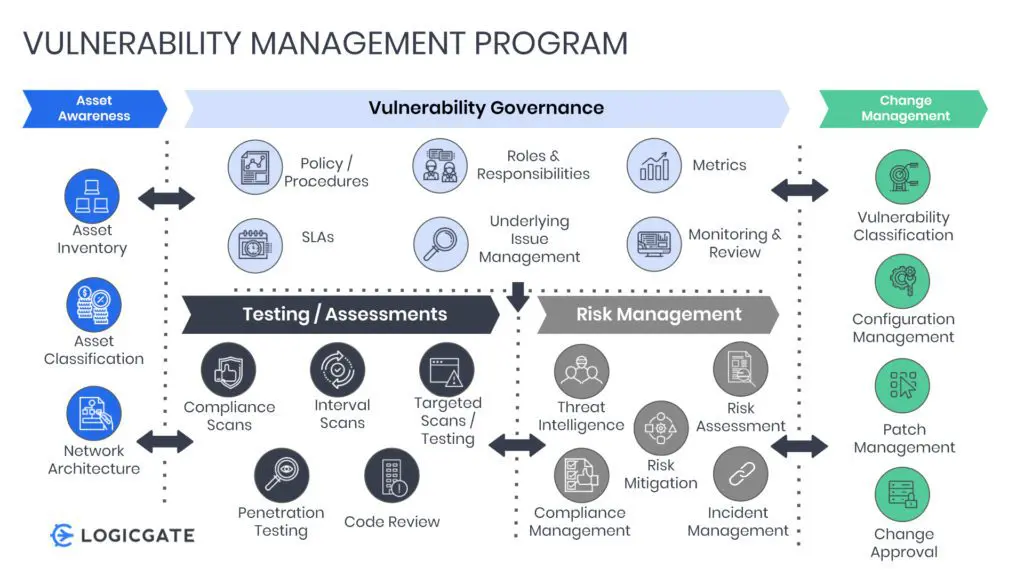
Defining a Holistic Vulnerability Management Program
Asset Awareness
Asset awareness is critical to the success of a holistic vulnerability management program. At the most basic level, awareness of the network architecture is key to performing vulnerability scanning. Advancing asset awareness over time by gaining a broader scope of asset inventories, and eventually asset classifications, will greatly help in fine-tuning not only what types of scanning should be conducted and how often, but also how to treat the vulnerabilities that are discovered via scanning and other testing/assessment activities.
These last two attributes of asset awareness will also enable your program to better conduct other functions within the holistic program such as risk management, compliance management, and determining how to best leverage threat intelligence within the program to drive more agile and targeted testing/assessments. For example, if threat actors begin to change which tactics they are using as entry points for ransomware, as well as which systems they are targeting, having asset classifications and inventories allows your organization to quickly create targeted tests for those threat scenarios and endpoint types where they exist within the infrastructure.
Vulnerability Governance
This area of a holistic vulnerability management program allows organizations to ensure proper alignment to the corporate priorities and mission, as well as providing higher-level visibility as needed to the executive team. It also establishes key performance guidelines in the form of established Service Level Agreements (SLAs) and metrics such as Key Risk Indicators (KRIs) and Key Performance Indicators (KPIs). Vulnerability governance helps organizations better understand underlying issues that may prevent your organization from being more efficient or effective in managing vulnerabilities including modifying testing, assessments, and risk management processes or techniques to overcome these issues.
Testing / Assessments
This function is one of the most utilized and generally understood functions of vulnerability management. However, if your organization hasn’t done so already, you should consider creating greater linkages between the various forms of testing being conducted to both the vulnerability governance as well as the risk management functions. For the former, tests should not only be guided by policies and procedures, but also have defined criteria for SLAs, with success measured by distinct vulnerability management metrics. With regard to the latter, not only should the testing function be incorporated into more holistic risk assessments and be a contributing factor to how risk is analyzed within the organization, but it is required to be completed for certain regulations or standards such as PCI. Creating the necessary relationships between threat intelligence, vulnerability determination, and association to specific assets is also key for organizations striving to develop a risk quantification capability, especially those leveraging the FAIR framework.
Risk Management
The testing and assessment types mentioned within the previous functional area do not necessarily identify all vulnerability types. For example, one of the top entry points for ransomware is email phishing. While definitely a vulnerability, it is not something that would normally be discovered by a vulnerability scan or by a penetration test. Rather it would typically require a more holistic technical risk assessment to find other areas of vulnerability not covered through scanning tools. A technical risk assessment can also determine if an email phishing vulnerability will require non-technical mitigation in the form of greater security awareness training, in addition to technical control implementation or changes in feature configuration settings within the email ecosystem. Leveraging findings from the testing/assessment function in conjunction with the more holistic risk assessment can also provide a more robust risk profile report for executive management that shows all potential areas of exposure to threats (like ransomware) and the ability to track that exposure through a common risk register.
Within the diagram, one might notice that threat intelligence is listed as part of the risk management functional area. While threat management and intelligence are commonly delivered outside of a risk team, threat information is necessary for fully analyzing risk and providing the proper focus for vulnerability management and testing. Creating the necessary relationships between threat intelligence, vulnerability determination based on specific threat actor/threat tactic pairings, and association to specific assets which may be targeted or susceptible to specific attack scenarios is essential. This insight will help your organization address specific weaknesses within your infrastructure that would be susceptible to those specific threats and become a critical time-saver.
Additionally, incident management is called out in this function for similar inter-related purposes where the team responsible for vulnerability management needs to understand linkages between testing and assessments and needs to create targeted tests based on incident-related activities. Ideally, incidents would serve as an internal real-time source of threat-related activity that may be associated with a specific threat event like ransomware and help fine-tune targeted testing based on areas of highest risk. Doing so would require relationships to exist between incident management, threat intelligence, risk assessments, and the testing/assessment functions of an organization.
Each of these functions may be handled by separate teams with separate platforms in your organization. Using a flexible GRC platform to manage both of these functions delivers the benefit of bringing all of the disparate data points together and automating some of the interdisciplinary activities and communications that will need to be executed in order for this to be successful.
Change Management
The final major functional area of a holistic vulnerability management program is Change Management. This function is essential for ensuring not only that patches are managed appropriately including testing of post-patch functionality, but also guides configuration management for proper hardening and feature enablement, classifying vulnerabilities to aid in prioritization of mitigation efforts, and change approval to ensure critical services are not disrupted during mitigation. Change Management in and of itself is another area where establishing communication across disparate teams is paramount to ensure all of your change stakeholders are aware of changes that need to be made, potential impacts of those changes as well as having well thought out back out procedures if or when the changes don’t go as planned.
Operationalizing Holistic Vulnerability Management
In order for a holistic vulnerability management program to be effective, it is necessary for many of the functions described above to work in concert, even when elements of these functions reside in different parts of the organization. As such it is important to streamline processes to create and maintain relationships between the disparate functions, groups, and data points. This includes clearly defined communication paths, roles, and responsibilities as well as the ability to track activities from end to end across the various groups. Where organizations struggle with operationalizing a holistic program like this is typically on two fronts:
- Not having enough skilled resources to conduct all functions efficiently and effectively
- Trying to maintain relationships and data across the disparate systems and groups required to execute the program in full
Addressing Resource Constraints
To address this first constraint, your organization should strongly consider leveraging a governance, risk, and compliance (GRC) platform that is capable of providing custom workflow automation. In doing so, many organizations have realized the benefits of a 20–50% reduction in the amount of time and resources it can take to execute the many necessary steps involved in a program such as this. By automating notifications and task management workflows, your organization can effectively eliminate manual and time-consuming activities. On top of that, by having a single system that can track these activities across multiple workgroups as well as consolidating key data points in a centralized system, the ability to create and track SLAs, KPIs, and KRIs related to the entire spectrum of holistic vulnerability management is easier and enables your organization to look for continued areas of improvement over time.
Addressing Internal Relationship Constraints
Creating and maintaining relationships across disparate teams has traditionally been difficult if not impossible even when leveraging legacy GRC platforms. Part of the reason for this is that most traditional GRC platforms leverage static data models and relational databases which make it difficult to create relationships, and are limiting when you need to change your processes over time to improve performance or broaden the scope of your programs. When this happens you are almost forced to start over from scratch rather than try to retrofit the static data model in all places where relationships were defined. By leveraging a GRC platform that supports dynamic data models through the use of a graph database, these traditional constraints can be overcome as a graph database treats relationships very differently and makes the creation and maintenance of those relationships easier for your organization as data points and groups change over time.
To further overcome relationship constraints, having a GRC platform that can conform to how your organization wants and needs to operate versus how a platform vendor believes it should be done can be a difference-maker for getting cross-organizational support in moving to a centralized platform. Organizations should seek out agile no-code platforms capable of adapting to your organization rather than the other way around and which are also able to change with you as your organization changes.
Ransomware has been difficult if not impossible for many organizations to address, partly as it is such a dynamic problem. In order to address such a dynamic problem, it requires a more holistic approach to vulnerability management and to be the most effective, will also require cross-organizational coordination. By centralizing disparate data points and cross-department workflows, your organization can overcome this challenge without monumental development costs and very likely can realize cost savings through task workflow automation.

