Protecting data is a critical priority for any organization. This year, the Department of Defense (DoD) specified an enhanced set of cybersecurity standards in order to protect sensitive, non-public data and secure the national defense supply chain. This framework was established in response to a growing number of threats, vulnerabilities, and cyberattacks at DoD contractors, which were being used by attackers as a backdoor to access DoD information assets.
The Cybersecurity Maturity Model Certification (CMMC) is a DoD framework specifying a unified set of cybersecurity standards required by DoD contractors, to ensure that the more than 300,000 companies in the defense industrial base (DIB) supply chain are protecting sensitive defense information assets.
The DoD will begin to migrate to this new framework by the end of the year in order to strengthen the cybersecurity practices of the DIB and ensure that a uniform set of protections are in place at the DoD, its partners, and contractors. Unlike previous cybersecurity standards for contractors, which were self-certified, CMMC will require third-party validation in order for a contractor to compete for DoD contracts. Once certified, the organization will be audited every three years to verify ongoing compliance.
CMMC Background
In 2018, Mitre Corp issued a paper, with the support of the DoD, called “Deliver Uncompromised: A Strategy for Supply Chain Security and Resilience in Response to the Changing Character of War.” In it, they highlighted the increasing level of threat to DoD cyber, network, and supply chain security, and how the DoD could partially address these vulnerabilities through the required implementation of stronger cybersecurity measures by all third parties with which it contracts.
In response, the DoD launched the CMMC Model 1.0 on January 31, 2020, to standardize how government contractors protect and secure DoD assets. The intention of this model is to establish robust and uniform security requirements as pre-existing criteria before reviewing competitive factors such as cost, performance, and schedule.
“Risk-based security should be viewed as a profit center for the capture of new business rather than a ‘loss’ or an expense harmful to the bottom line.”
— Mitre Corp in its paper “Deliver Uncompromised: A Strategy for Supply Chain Security and Resilience in Response to the Changing Character of War.”
Who is Affected by CMMC
CMMC guidelines will apply to all parties in the defense supply chain, including contractors, vendors, any third parties included in contracts, and related organizations that support the DoD.
Though the July deadline was delayed due to COVID-19, starting toward the end of 2020, an organization must be certified at the required level for the DoD to consider their RFP.
Purpose of CMMC
CMMC is a unified cybersecurity framework for future DoD acquisitions. Its intent is to embed uniform procedures and cybersecurity best practices into a set of specified domains.
Per the DoD, the CMMC will be incorporated into Defense Federal Acquisition Regulation Supplement (DFARS) and used as a requirement for contract awards. Its intent is to serve as a verification mechanism to i.) ensure appropriate levels of cybersecurity practices and processes and basic cyber hygiene and ii.) protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
DoD contractors have access to two types of information: Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
CUI is information that requires safeguarding or dissemination controls pursuant to and consistent with laws, regulations, or government-wide policy. The CUI Registry covers the specific types of information that must be protected under a long list of categories spanning from Critical Infrastructure, Defense, Immigration, and International Agreements to NATO, Nuclear, and Tax information.
FCI or Federal Contract Information is information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government.
Not every organization will handle CUI, but every DoD contractor will have access to FCI when it works with the Government. As such, they must employ a minimum level of cybersecurity as detailed in the CMMC.
CMMC Framework
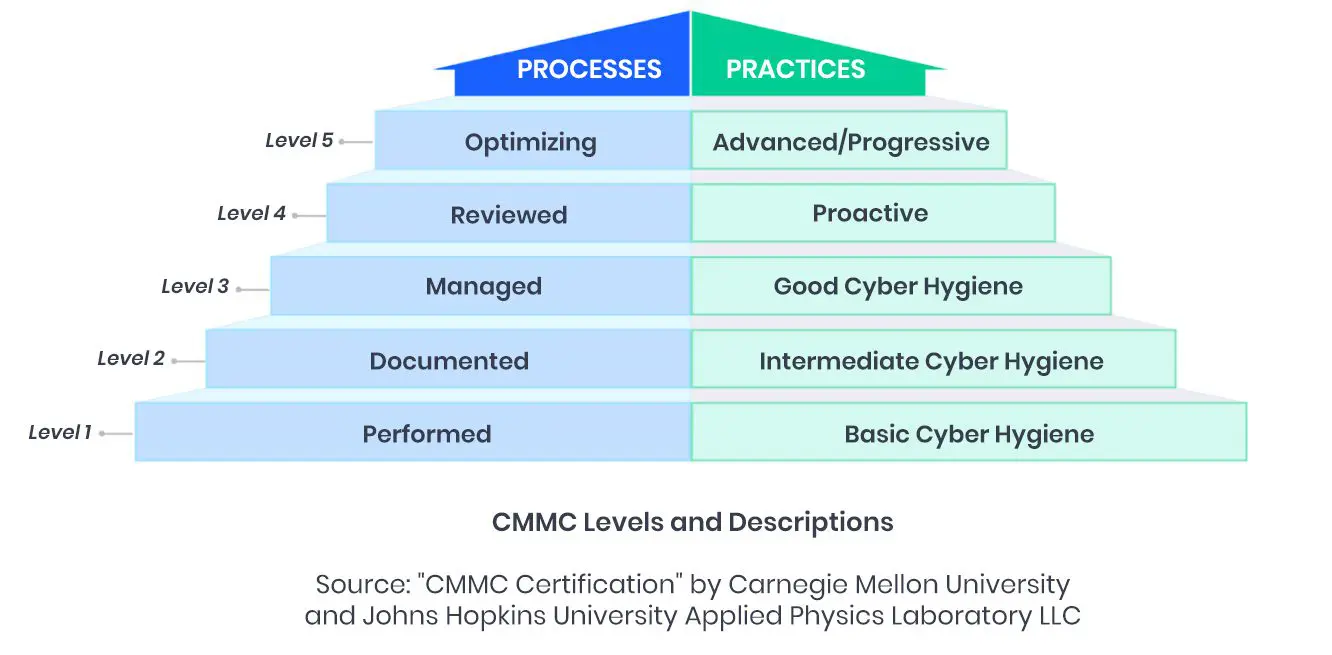
The CMMC encompasses five levels of maturity ranging from “Basic Cybersecurity Hygiene” to “Advanced/Progressive”. Each level maps to a specific capability. To progress to the highest level, a contractor must demonstrate proficiency in the preceding levels.
Level 1: Basic safeguarding of FCI
Level 2: Transition step to protect CUI
Level 3: Protecting CUI
Levels 4-5: Protecting CUI and reducing risk of Advanced Persistent Threats
Every DoD contractor will have access to FCI when it works with the DoD. As such, they must have a minimum Level 1 certification, with each progressive level allowing them to bid for contracts that provide access to increasingly controlled data and require higher levels of security.
The CMMC framework encompasses 17 domains as follows:
- Access Control (AC)
- Asset Management (AM)
- Audit and Accountability (AU)
- Awareness and Training (AT)
- Configuration Management (CM)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Recovery (RE)
- Risk Management (RM)
- Security Assessment (CA)
- Situational Awareness (SA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
Each domain consists of a set of processes, capabilities, and practices across the five levels. Some of these were specified under previous DoD requirements including FAR Clause 52.204-21 and NIST SP 800-171 and may already be established at your organization. The CMMC framework goes a step further to ensure these guidelines are institutionalized, implemented, and able to be repeated consistently and appropriately. Further details on CMMC required capabilities, processes, and practices can be found in this report from Carnegie Mellon University and Johns Hopkins University Applied Physics Laboratory LLC.
How to Prepare for CMMC
Once you have identified the level of certification required for your organization’s current or prospective DoD contracts, you will need to evaluate strengths and address vulnerabilities in your cybersecurity processes and practices. A GRC platform can help facilitate the CMMC process in the following areas:
- Threat Assessment – Evaluates strengths, vulnerabilities, and gaps in existing cybersecurity practices for CMMC readiness.
- Process Management – Provides a centralized information security risk management tool and platform to effectively manage processes and practices across specified domains.
- Access Control – Manage differentiated access to CUI with varying levels of approvals across individuals or departments.
- Incident Reporting and Mitigation – Provide relevant parties the reporting, incident management, and mitigation tools needed to safeguard DoD assets.
- Cross-divisional collaboration – Facilitate collaboration, coordination, and information sharing across divisions to ensure effective compliance.
- Reporting – Serve as a repository for information required by DoD for third-party verification or auditing purposes.
Given the critical national importance of DoD information security and the impending deadline for enhanced cybersecurity requirements for all DoD contractors, a GRC platform provides the process enhancements and visibility needed to assess your areas of readiness, implement, and institutionalize CMMC requirements, prepare for third-party validation, and maintain ongoing compliance.