Whether you’re looking to win new business as a vendor or mitigate risks as a customer, vendor security reviews are essential to Software as a Service (SaaS) sales and third-party risk management (TPRM). Unfortunately, the necessity of these assessments doesn’t lessen the burden on those responsible for conducting or responding to them.
Why Should You Streamline the Vendor Review Process?
Risk and compliance teams must manage a growing scope of work in today’s vendor-dependent work environment. This makes manually requesting, tracking down, and reviewing documentation a hindrance to higher-impact activities — no matter which side of the assessment you’re on.
Finding practical ways to streamline the security review process can save your organization time and energy. Then, you can reallocate those newfound resources to activities that keep your GRC programs ahead of technology and threats. But if your team is stuck in day-to-day manual tasks, you’re missing opportunities to mature your overall security program.
“If you’re not actively improving your risk management programs, you’re getting worse. There’s no such thing as maintaining the status quo because technology and threats are constantly advancing, you’re going to get lapped by everyone else.” – LogicGate’s Enterprise Security Analyst
How to Streamline Vendor Reviews: The Science
The heavy toil of vendor reviews bogs down your efficiency, preventing you from advancing and maturing your overall security program. To avoid this trap, consider these recommendations from one of LogicGate’s Enterprise Security Analysts.
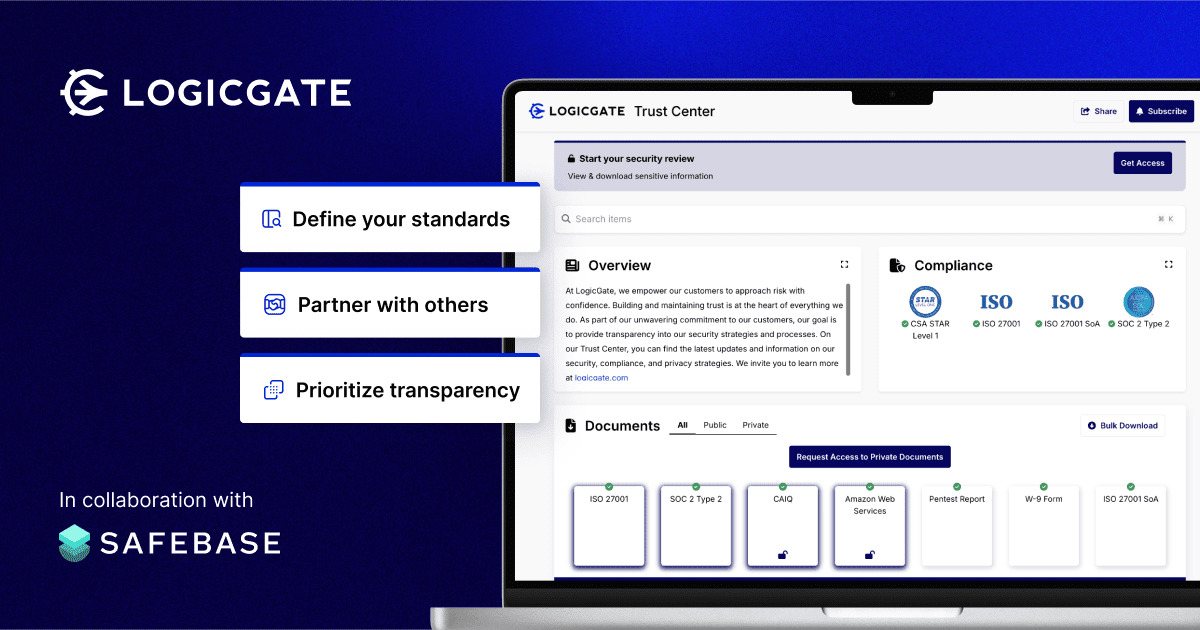
1) Define Your Standards
The foundational element of any effective and efficient TPRM program boils down to clear standards and procedures. Not all vendors are created equal, so why should your process treat them as such? Clearly define your expectations, risk tolerance, and review process for the common vendor types your organization seeks to partner with. This will help teams create an appropriate scope of work for each assessment, as well as:
- Save time by minimizing redundant or unnecessary work
- Identify risks that fall outside of your risk tolerance
- Accept and monitor risks your organization is willing to take
“The concept of diminishing returns is very relevant here. If you are reading every single line of every possible document for every single vendor, you could be reading hundreds of pages for every single review. That may not be the best use of your time.
It’s true that every vendor is different, but they ultimately fall into a handful of categories. It’s extremely helpful to understand and standardize what key pieces of information you need for each of those different groups.” – LogicGate’s Enterprise Security Analyst
2) Join Forces With Other Risk Leaders
As you formalize or optimize your third-party risk management process, be sure to look for ways to partner with your enterprise risk management (ERM) function. Although third-party risk teams often have the “blocker” reputation, there’s a significant opportunity to shift the narrative and step into the role of a consultant.
“The business is allowed to take risks. Your security function, including third-party risk management, is here to serve the business. It’s possible that you are reviewing a vendor that doesn’t meet the absolute highest security standards but you have to assess any risks in the context of your organization’s business objectives.
This is an opportunity for you to shift from a gatekeeper to a consultant — advising your leaders on what could happen by partnering with said vendor and empowering them to strategically accept or reject any risks.” – LogicGate’s Enterprise Security Analyst
This is why defining standards is critical — without a clear understanding of risk tolerance within the context of the vendor type, it’s more challenging (or almost impossible) to assess how a new partnership will impact your organization’s strategic objectives.

Real-Life Example: United Community Banks, Inc
United Community Banks, Inc. (UCB), one of the largest full-service financial institutions in the southeast United States, came to LogicGate looking to mature their existing enterprise risk, third-party risk, and controls compliance programs. Through a GRC maturity workshop, the group identified that their ideal future state would include:
- Driving tactical coordination and visibility of risk between departments
- Empowering the business to make risk-informed decisions
A core aspect of the two-year maturity roadmap included identifying and linking GRC datasets to connect the enterprise risk function and operational groups, like third-party risk management. By consolidating information across teams, risk leaders improved their ability to provide practical guidance to the business to promote risk as a business enabler.
3) Prioritize Transparency to Maximize Time Savings
Vendor reviews aren’t a static process. As your review workflows and buyer expectations change and adapt, so should your capacity to handle them. Creating a single source of truth for all program standards, processes, and data builds a level of transparency that makes it possible to efficiently and effectively adapt over time.
A Trust Center allows you to make security documentation centrally available without compromising security. Trust Centers automate several aspects of the security review process while enabling buyers to self-serve pertinent security information, making the process easier, quicker, and less painful for everyone involved.
Real-Life Example: Instacart
Instacart, a leading grocery technology company, struggled with repetitive questionnaires, an inefficient NDA process, and stakeholders sharing outdated information. Sound familiar? By partnering with SafeBase, Instacart built their Trust Center, enabling sellers to:
- Confidently point prospects to the up-to-date security documents instead of reaching out the security team for help
- Streamline the NDA process with SafeBase’s built-in Clickwrap NDA feature
This has allowed Instacart’s security and legal teams to cut down on custom questionnaires, email inquiries, and NDA approvals — saving an approximate 5,000 hours per year.
[Read More SafeBase Success Stories]
Partnering Through Trust: The Art
From personal life to business, trust is a critical aspect of any relationship. This makes risk management equally an art and science. Instilling trust with customers and colleagues, both internally and externally, goes a long way in forming a credible reputation.
“Trust is an experience. Allowing your customers to easily access the information they need when they need it? You’re not just communicating or validating your organization’s security posture — you’re creating an experience deeply rooted in trust.” -SafeBase CEO Al Yang
We want to help our customers succeed in their vendor reviews while taking our own advice and saving time through transparency. That’s why we were excited to partner with SafeBase to launch our official LogicGate Trust Center!
“When I see that a vendor I’m reviewing has a trust center, I breathe a sigh of relief. I know that instead of sending a bunch of emails and waiting for a reply (especially if we need to sign an NDA) the process will only take a couple of days instead of potentially several weeks. It’s also reassuring to see that the vendor’s security team is so organized and makes their latest documentation readily available. The fact we can now offer this convenience to our own customer base is very exciting.” – LogicGate’s Enterprise Security Analyst
Streamlining vendor reviews isn’t just about saving time — it’s about reclaiming bandwidth. With clearly defined standards, collaborating across risk functions, and transparency first, you’re equipped to elevate your security program. An improved vendor review process means reduced manual work, more focus on strategic growth, and staying ahead of the technological curve.
The more efficiently you manage vendor reviews, the more room you create for innovation and long-term success.