Expanding into the public sector to do business with federal agencies can be a lucrative play for any organization, but being able to do that depends on your ability to become FedRAMP certified. Meeting these federal cloud security requirements is simply not optional for cloud service providers seeking to contract with the U.S. government.
Obtaining FedRAMP certification is easier said than done, however. It requires a significant investment of planning, time, and resources. Here’s our guide to FedRAMP’s certification process and how modern GRC technology can lighten the lift.
What is FedRAMP?
FedRAMP (The Federal Risk and Authorization Management Program) regulates the necessary processes for vendors to secure their cloud services and offerings for the federal marketplace under the requirements of FISMA (the Federal Information Security Modernization Act).
Any cloud service provider (CSP) seeking to provide a cloud service offering (CSO) to U.S. federal agencies must first receive FedRAMP certification. A CSP’s most crucial step in preparing for the FedRAMP certification process is establishing a System Security Plan (SSP).
FedRAMP SSP
Developing a FedRAMP SSP presents unique challenges for each cloud service vendor and their offering(s). Fortunately, tools and resources are available to centralize your organization’s efforts and efficiently navigate your journey to FedRAMP certification. This article offers a FedRAMP compliance checklist to identify and prioritize the next steps for your organization to build your FedRAMP SSP.
FedRAMP SSP compliance checklist
A FedRAMP SSP is a complete record of the security controls for a CSP and CSO that demonstrates individual control compliance with FedRAMP requirements.
An SSP is established by a CSP and used by federal agencies, the FedRAMP Joint Authorization Board (JAB), and Third-Party Assessment Organizations (3PAOs) to assess the CSP’s security systems.
Every CSP will need the following to complete a FedRAMP SSP:
- The required SSP template provided by FedRAMP
- Documented third-party assessments of the SSP against cloud services and offerings
- A standardized approach for conducting CSO evaluations and audits of the SSP
Every CSP will not need the same FedRAMP standard of authorization:
FedRAMP evaluates CSOs based on how severely an agency could be impacted by a loss in that CSO’s data: confidentiality, integrity, and availability. Depending on the level of potential risk, FedRAMP authorizes CSOs at three Impact Levels:
- Low Impact Level: For systems with low-impact data where a loss or breach would cause limited adverse effects on an agency’s operations, assets, or individuals.
- Moderate Impact Level: Most (80%) of CSOs with FedRAMP certification are at the Moderate Impact Level. This is most appropriate when a loss in confidentiality, integrity, or availability could seriously affect an agency’s operations, assets, finances, or individuals.
- High Impact Level: Typically, organizations requiring a High Impact Level authorization from FedRAMP are located in fields like healthcare, law enforcement, and emergency services. The High Impact Level is reserved for CSOs interfacing with sensitive government data where security risks could result in severe or catastrophic adverse effects for an agency.
What is included in the FedRAMP SSP?
Each Impact Level above has a corresponding SSP template available from FedRAMP.
The templates are exhaustive and can seem overwhelming to an organization new to the SSP process. Reviewing these templates in and of themselves can be a roadblock for organizations, as it requires significant coordination of internal teams and information.
To complete a FedRAMP SSP, a CSP should have the ability to define the following at a minimum:
- SSP implementation details
- Inventory of a CSO’s network of data relations and connections
- The CSO’s security authorization limits and boundaries
- All controls implemented and their implementation processes
- Planned controls and implementation details
- CSP roles, responsibilities, and control ownership details
- System information (user types, protocols, services, etc.)
- Contingency plans for specific controls
- Federal agency roles and responsibilities related to the SSP
FedRAMP authorization process
Every CSP will pursue FedRAMP authorization in one of two ways:
- Through an Individual Agency (image: “Agency Process”)
To obtain an Agency Authorization to Operate (ATO), a CSP can partner directly with a federal agency during the pre-authorization for a CSO.
- Through the Joint Authorization Board (JAB): (image: “JAB Process”)
JAB is the primary authorizing body for FedRAMP. Achieving a JAB Provisional Authorization to Operate (P-ATO) for a CSO requires intensive pre-authorization assessments. Still, it results in more confidence for agencies in the federal marketplace.
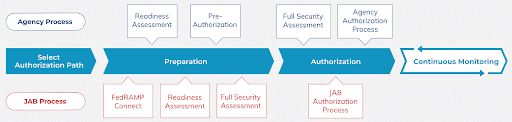
Regardless of the path you take to authorization, the scope of the FedRAMP SSP development process can seem daunting. But, there are some clear first steps that you can take.
Your FedRAMP SSP next steps
Align internal information and documentation
In the “Preparation” phase of the FedRAMP authorization process, a CSP must compile a significant amount of detailed information and create diagrams for use in the FedRAMP SSP and related evaluations. This includes the following:
- Diagram Network Architecture: Creating a total network architecture diagram outlining all aspects of the network’s security configuration.
- Compile System Inventory: Complete an exhaustive inventory of all hardware and software, and ensure that the inventory references each system component included in a network or data diagram.
- Diagram All Data Flows: Emphasize visually any point where system data can be accessed or could exit a secure system boundary or bypass a control.
- Document Control Implementation Details: Ensure all controls related to a CSO must have established implementation and evaluation plans. Aligning controls to the appropriate compliance requirements can be made easier by utilizing an RTM (Requirements Traceability Matrix) to track the completion of your control descriptions.
- Coordinate All Responsible Parties: It’s common for CSPs to have shared authorization and security responsibilities with external parties. You must ensure that each responsibility shared with another party is defined as such, along with the related shared controls.
Establish Your SSP Implementation Team
Accomplishing the tasks needed to comply with authorization and complete an SSP requires dedicated participation from multiple business functions and units. Launching the FedRAMP SSP processes requires an interdisciplinary team who can delegate tasks, coordinate efforts, and identify areas where external resources or consultants are needed.
The members of an SSP Implementation team need to have deep domain expertise and advanced knowledge of cloud computing security, network architecture, and diagramming They must also be able to document and communicate that information clearly and accurately.
Utilize FedRAMP Software Solutions to Help
Whether you are preparing your FedRAMP SSP or are in the process of continuous monitoring for an existing SSP, the right software solution can alleviate much of the strain. Maintaining documents and spreadsheets for a process as intensive as FedRAMP authorization is tedious and can expose an organization to inaccuracies and setbacks.
Utilizing a software solution for team members preparing and implementing an SSP can streamline the FedRAMP audit and SSP generation process. Having a single repository for all components and documentation enables the SSP team to check the progress of an audit, see outstanding tasks, and prioritize the next steps.
Risk Cloud’s FedRAMP SSP solution helps organizations accomplish all of the above. Additionally, Risk Cloud enables organizations to:
- Automate document generation from a centralized data repository
- Bulk update documents and attachments with multiple iterations of copies.
- Automate communications, notifications, and requests for evidence or information and create accountability with team members and stakeholders.
- Generate reports on asset ownership and review the effectiveness of collaboration.
- Centralize control evaluations and review against stored frameworks and templates for compliance.
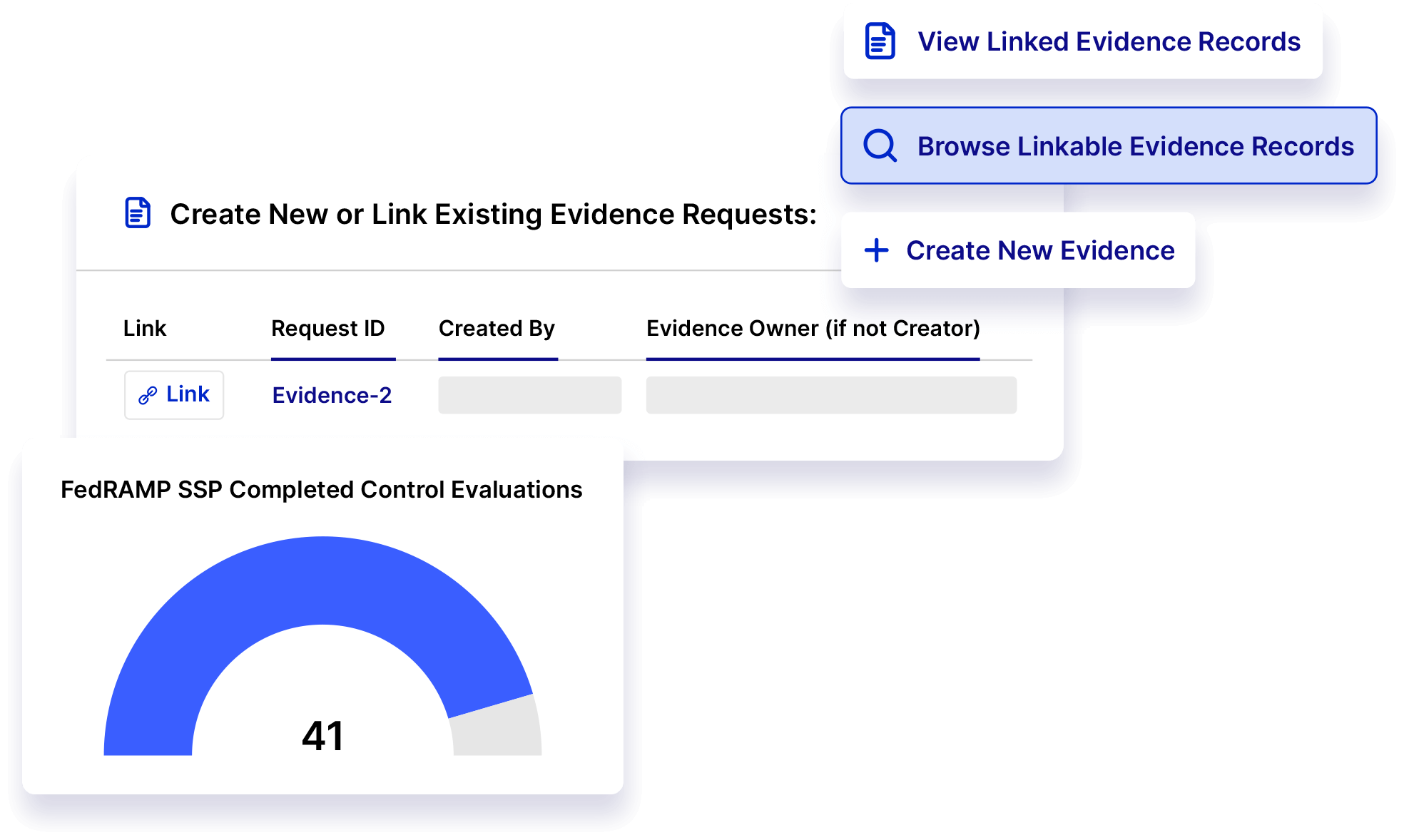
Manage Continuous Compliance Monitoring & Track Remediation Efforts
Once a CSO receives FedRAMP authorization, it will require the CSP to manage compliance and track remediation efforts continuously. A software solution like Risk Cloud enables CSPs to expedite SSP reassessments with an integrated inventory and assets and maintain constant visibility of their security posture.
Ready to enhance your risk management and compliance capabilities? Schedule a demo of Risk Cloud’s FedRAMP SSP Application today.
