Vulnerability Management Application
Avoid downtime and protect critical assets with automated vulnerability logging, impact assessments, and mitigation planning workflows.
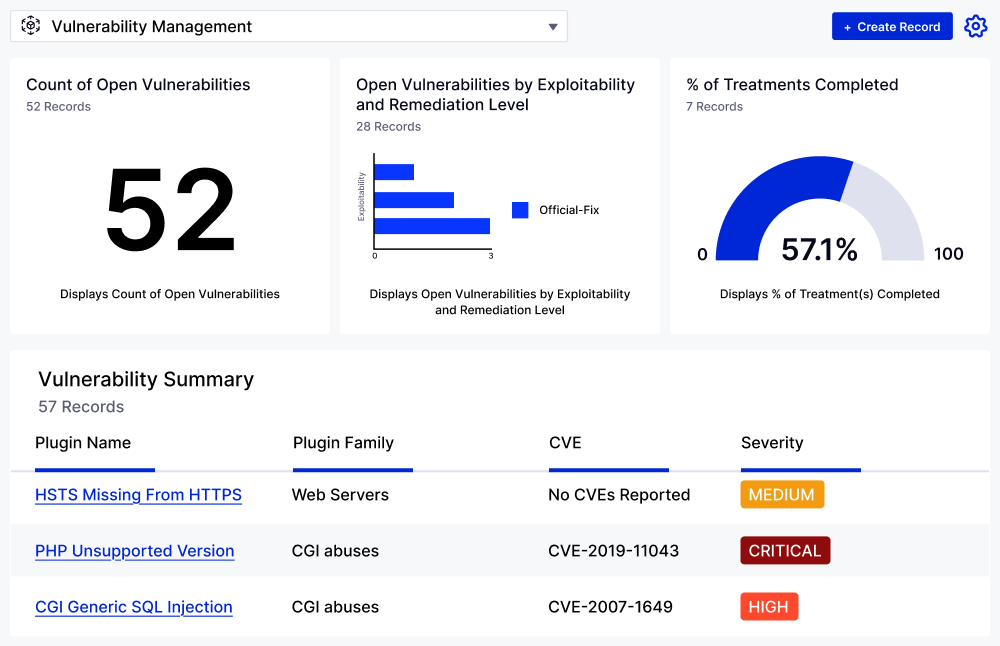
What is the Vulnerability Management Application?
The Application centralizes the vulnerability management process, automates workflows, and enhances collaboration to ensure timely responses. With real-time insights and reporting capabilities, the Application enables organizations to better protect their assets and effectively minimize risk.
Centralize Vulnerability Logging, Impact Assessment, and Treatment
Prioritize treatment plans and reduce risk at your organization through an integrated platform for tracking assets, vulnerabilities, and mitigations.
Gain Near Real-Time Visibility into Your Organization’s Most Critical Vulnerabilities and Assets
Stay ahead of the latest threats by automatically pulling vulnerability information, such as descriptions and severity, from tools like Tenable.io, Qualys, CrowdStrike, and Rapid7. Centralize assets, related vulnerabilities, assessment activities, and treatment plans for near real-time visibility into inherent and residual risk within your organization.
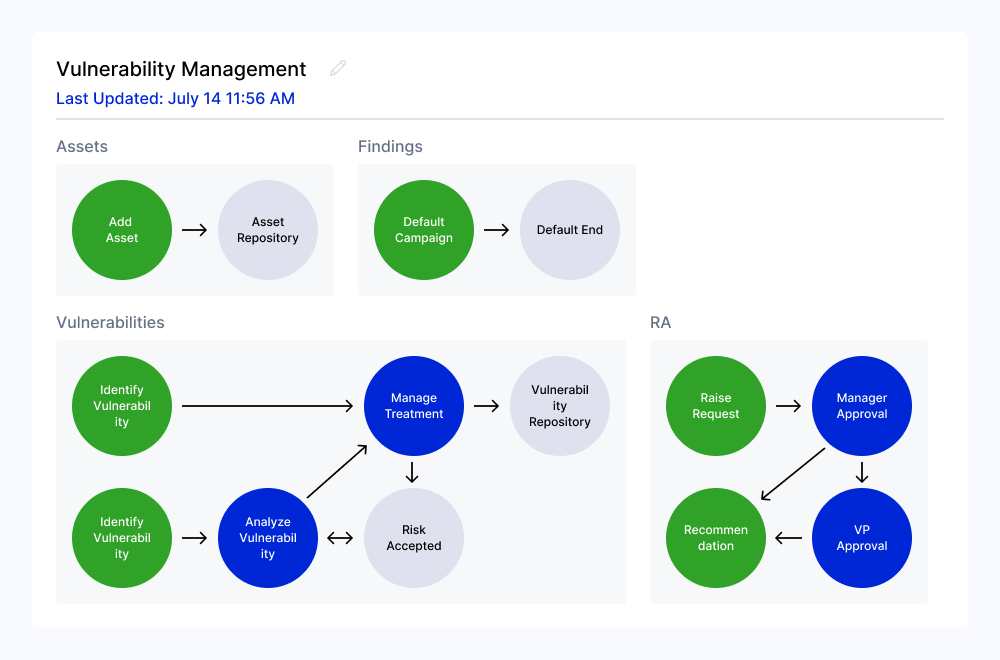
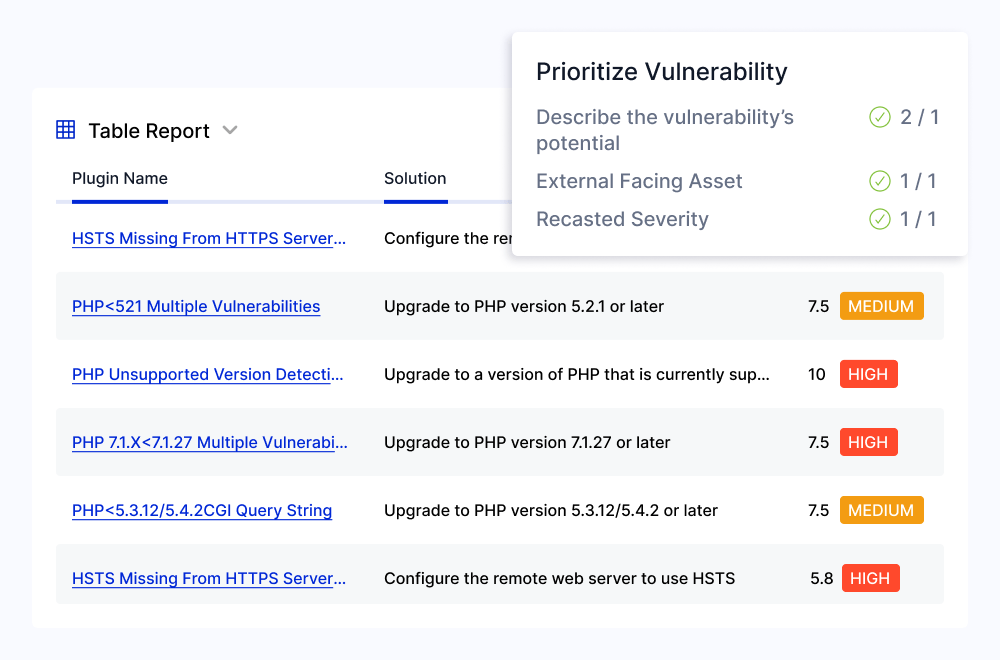
Accelerate Vulnerability Analysis and Treatment with Scalable, Automated Workflows
Notify teams about critical vulnerabilities as they are discovered, assess business impact, and assign treatment plans using automated workflows. Simplify the review process with a consolidated view of all relevant vulnerability information and keep teams informed with assignment notifications and reminders in tools like Slack, Jira, and Microsoft Teams.
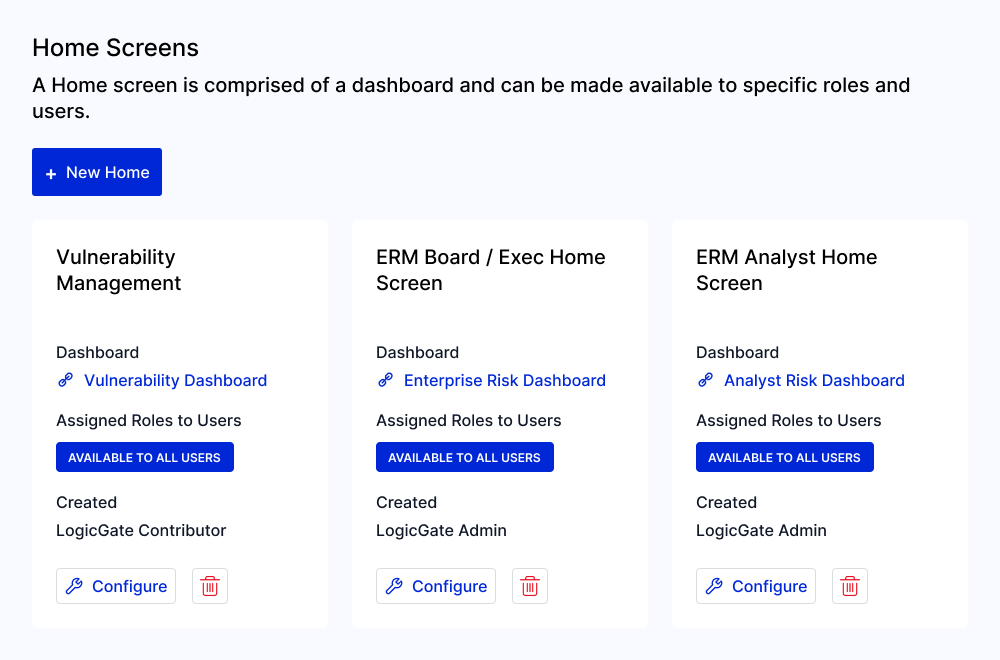
Streamline Vulnerability Reporting with Role-Based Dashboards
Centralize and transform data into actionable insights with customizable reports tailored to your needs. Visualize critical metrics such as open vulnerabilities, severity levels, treatment statuses, and fixes over time. Enhance stakeholder communication through role-based dashboards that display relevant information for each audience.