Third-Party Risk Management Application
Gain the visibility you need to safely onboard new vendors while streamlining assessment, risk mitigation, and offboarding processes.
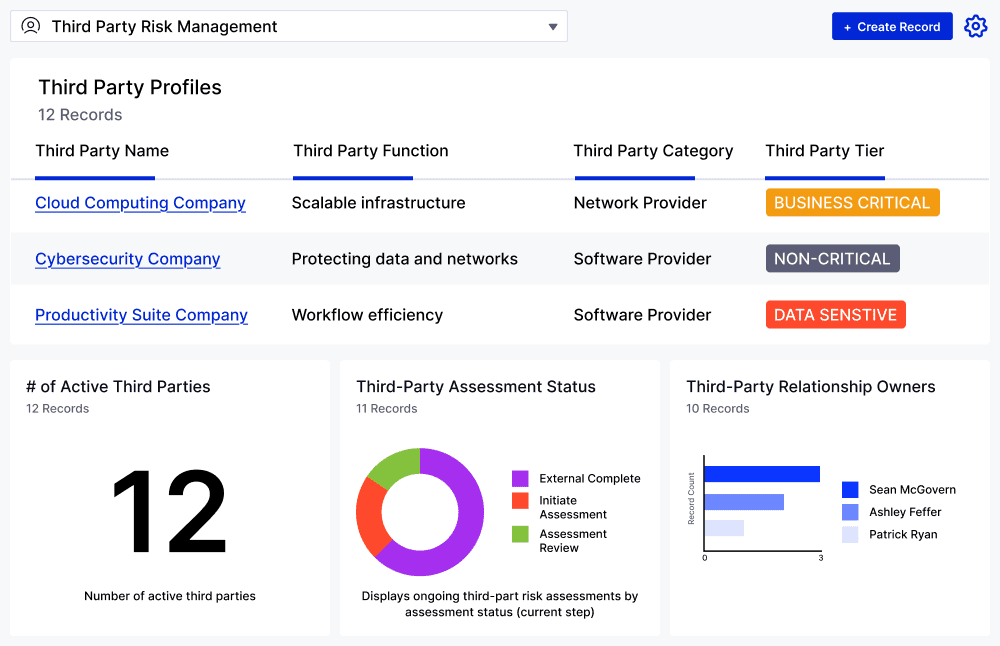
What is the Third-Party Risk Management (TPRM) Application?
The Application provides the visibility needed to safely onboard new vendors while streamlining assessment, risk mitigation, and offboarding processes. This Application saves teams time with out-of-the-box questionnaires aligned to industry standards — like SIG, NIST, and CAIQ — automated workflows, and near real-time reports on third-party risk.
Efficiently Scale and Mature your Third-Party Risk Management Program
Easily assess third-party risk impact and prioritize mitigation strategies with a centralized and automated approach to TPRM.
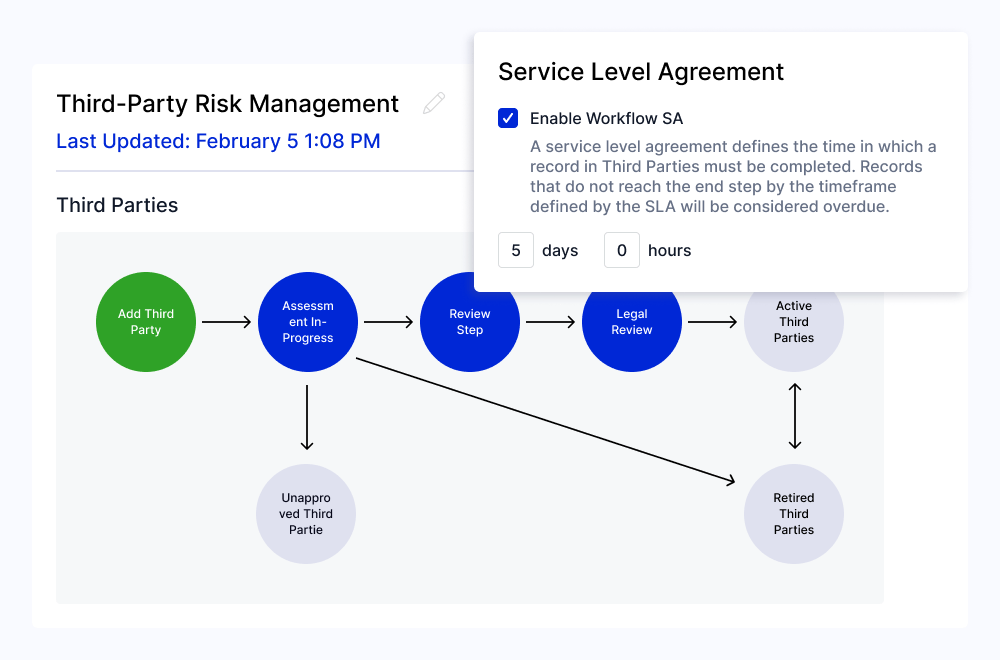
Accelerate Vendor Onboarding
Streamline new vendor requests with a standardized intake form that automatically identifies data-sensitive and business-critical third parties. Accelerate the risk scoring process with pre-built assessments that calculate a recommended risk score based on vendor attestations. Use any of the following out-of-the-box questionnaires or configure them to meet your program’s unique needs:
- SIG Lite, SIG Privacy, SIG ESG, SIG AI
- NIST CSF
- Consensus Assessment Initiative Questionnaire (CAIQ)
- LogicGate’s Third-Party Risk Management Question Bank
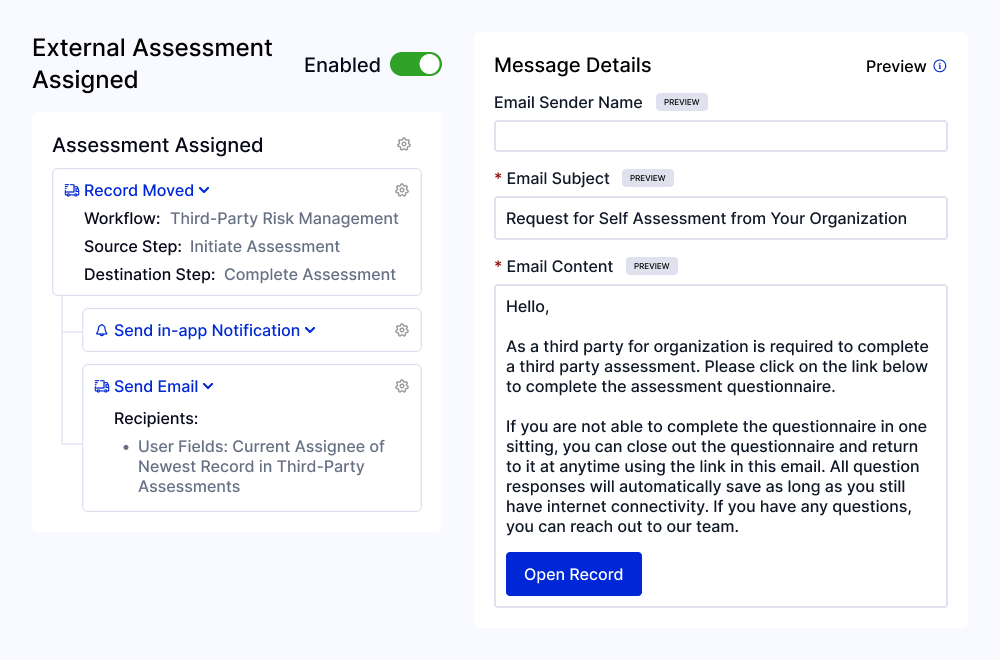
Simplify Internal and External Collaboration
Create a process your stakeholders can easily adopt — from relationship owners and risk managers to third-party contacts. Risk Cloud® helps you:
- Keep assessments and resolutions on track with assignment notifications and automatic deadline reminders
- Support timely completion with easy-to-use questionnaires optimized for completion and secure third-party access
- Standardize scoring with built-in vendor tiers, assessment scores, and risk levels that can be further tailored to your organization’s unique needs
- Securely offboard vendors with a standardized task list and built-in review
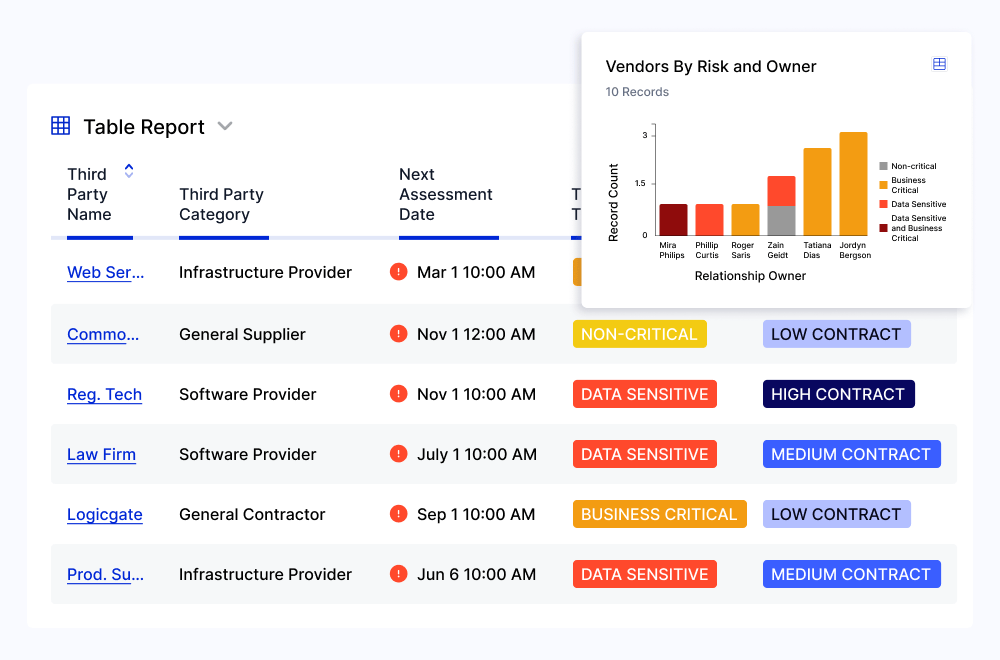
Stay On Top of Third-Party Vulnerabilities
Quickly identify the impact of third-party incidents or vulnerabilities with a compromise assessment questionnaire that automatically kicks off an internal review process. Strategically prioritize mitigation response based on compromise impact assessment scores. Track team progress with a centralized view of external vulnerabilities by publication date, compromise impact assessment status, and third parties with impacted platforms.
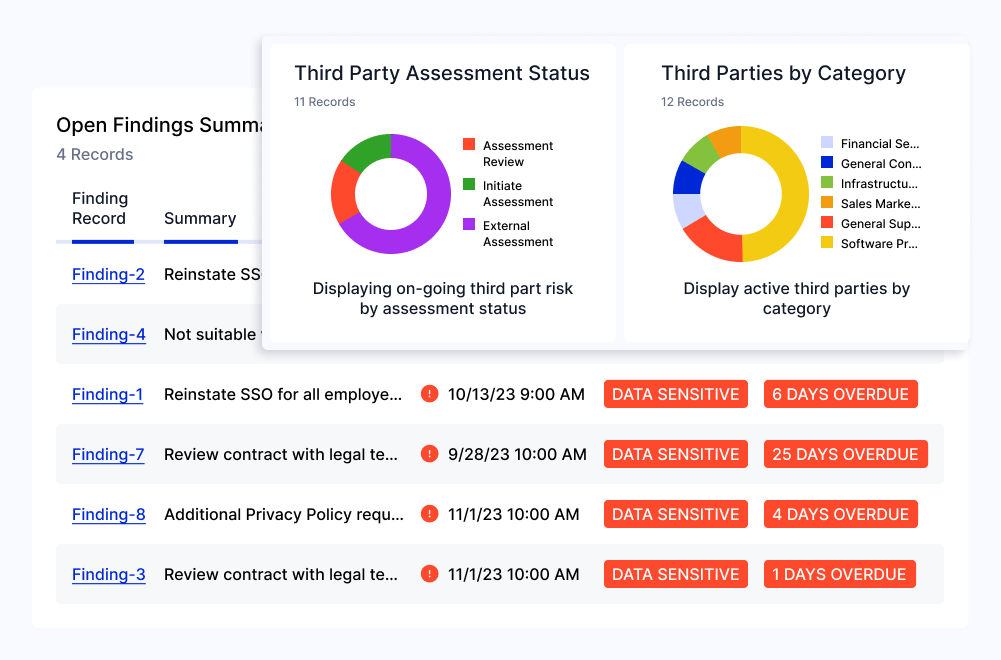
Create a Holistic View of Active Third Parties
Quickly visualize vendors, assessment status, risk scores, active vulnerabilities, and resolution progress in a single platform while:
- Maximizing your insights by integrating with intelligence providers like Black Kite, SecurityScorecard, and Vital4.
- Effectively identifying and mitigating your most critical third-party risks with AI-generated vendor summaries.
- Building stakeholder buy-in with easy-to-read dashboards that highlight success metrics and KPIs.