Penetration Testing Application
Uncover and mitigate vulnerabilities faster with a centralized and streamlined approach to penetration testing , from scoping to remediation tracking.
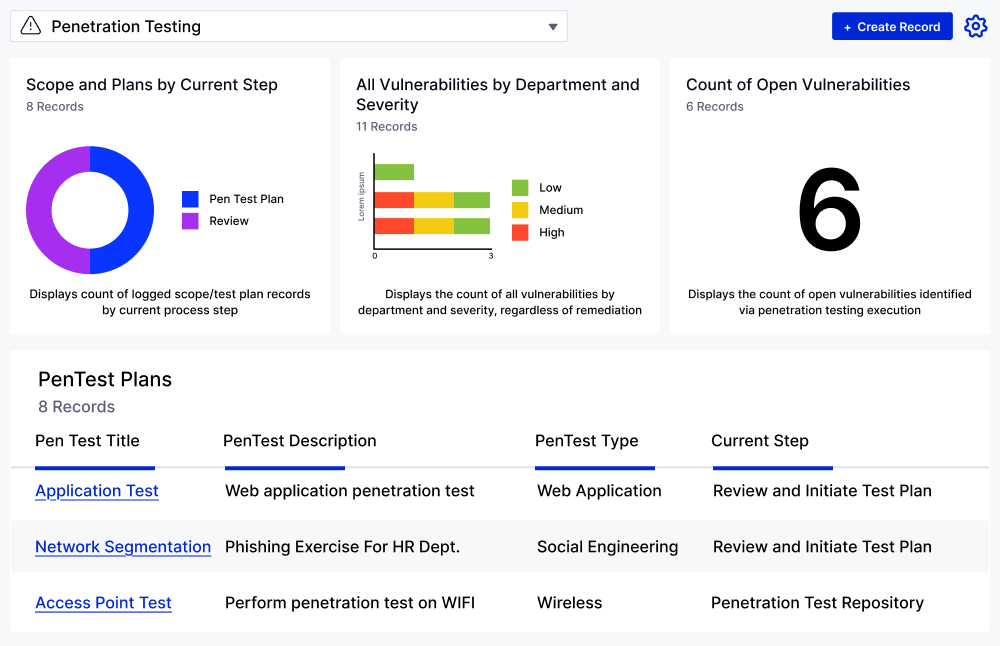
What is the Penetration Testing Application?
The Application enables teams to avoid critical security issues through automated workflows, real-time insights, and efficient vulnerability management.
Identify and Remediate Vulnerabilities Before Incidents Occur
Minimize manual labor associated with traditional pentesting workflows by automating notifications, reminders, and reporting while standardizing processes to help teams identify and mitigate vulnerabilities in less time.
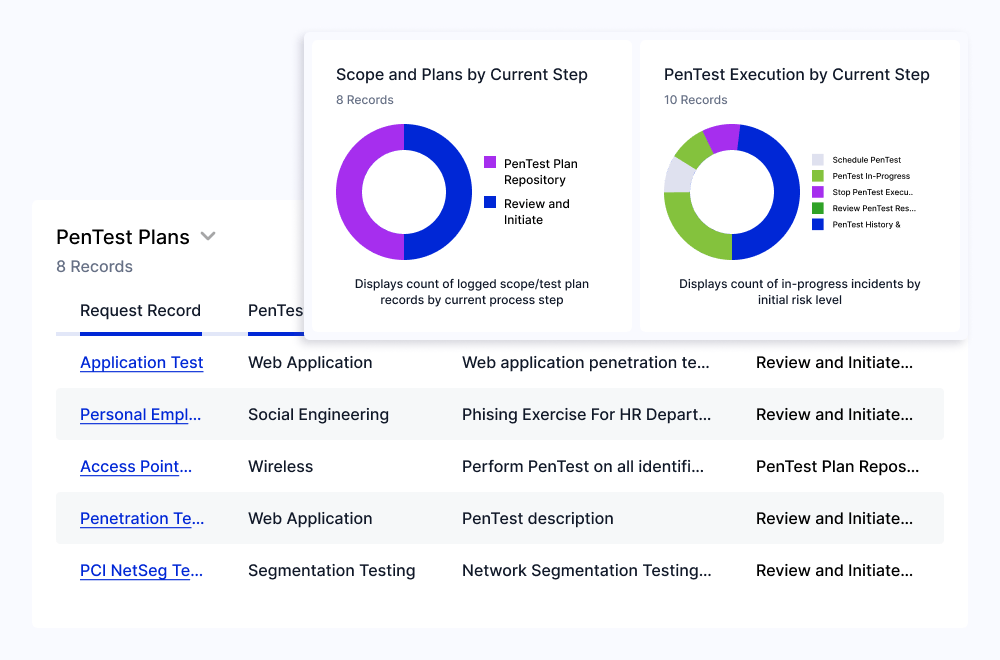
Plan and Execute Effective Penetration Tests
Collect and document key penetration testing information, such as test scope and your planned test approach. Stakeholders can review and approve pentesting information before testing to ensure processes are effective.
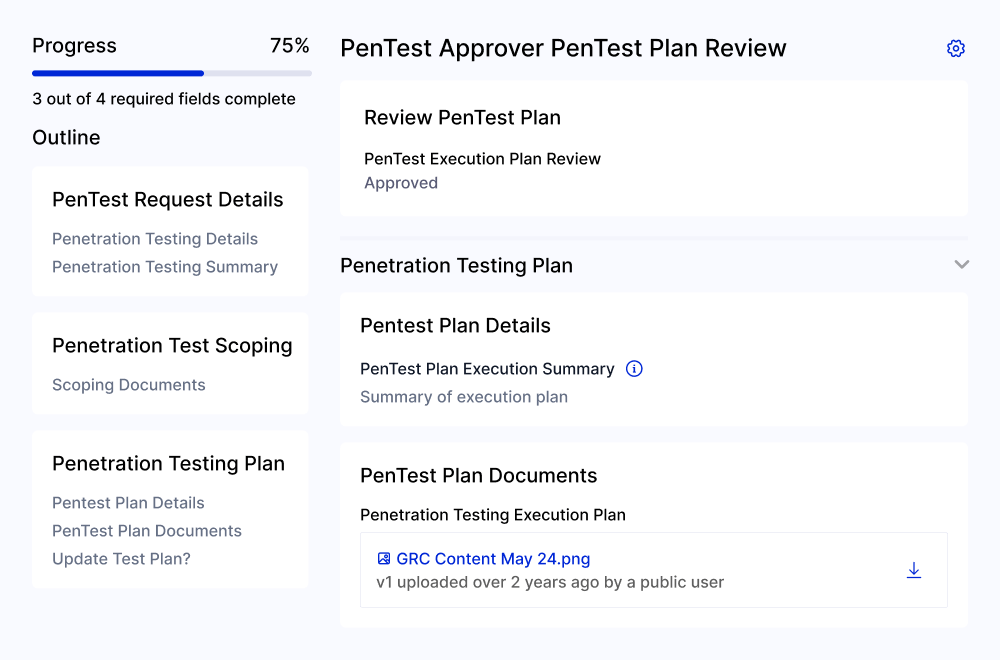
Gain Better Visibility and Save Time On Your Pentesting Processes
Consolidate all findings,track progress,view results in a centralized location for better visibility so you can complete penetration tests more efficiently. Reduce the time spent gathering historical test information for future tests.
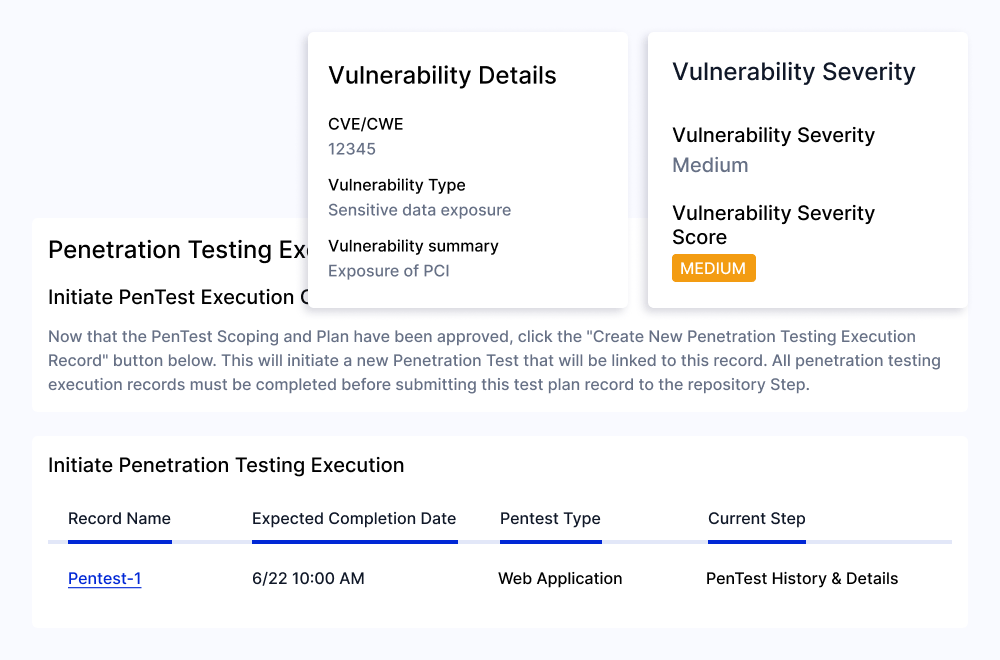
Take Action on Findings and Remediate Critical Vulnerabilities
Review any identified vulnerabilities and determine whether remediation efforts are required based on type, severity, and impact. Assign tasks to responsible stakeholders and enable automatic notifications on vulnerability remediation deadlines and future penetration tests.
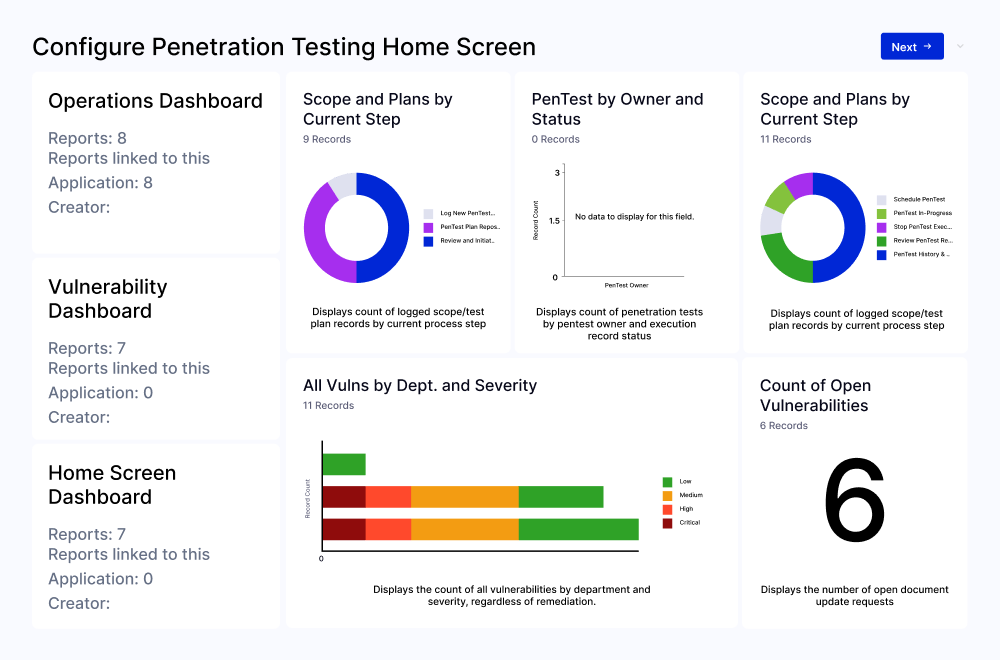
Improve Decision Making and Communication With Pre-Built Reports
Generate pre-built and custom reports to track the status and findings of penetration tests. It features over a dozen user-friendly dashboards detailing open vulnerabilities by department, remediation status, severity, and more, simplifying the process of identifying and addressing security issues.