Keeping sensitive data secure and navigating the ever-expanding web of privacy and security regulations often feels like a never-ending, uphill battle. The HITRUST Common Security Framework (CSF) has been a cornerstone for many healthcare organizations for well over a decade, offering a comprehensive and certifiable approach to risk management and regulatory compliance. But in a world now grappling with the complexities of Artificial Intelligence and ever-more sophisticated cyber threats, you might be wondering: is it still relevant? Having just emerged from the intensive HITRUST CSF assessor training and certification process myself, I can tell you with a fresh perspective: not only is it relevant, but it’s also evolving in critical ways to meet these new challenges head-on.
For years, HITRUST provided a solid blueprint for organizations, helping to ensure sensitive information stayed locked down and regulatory obligations were met. But what happens when the nature of the threats changes, when the very tools we use to conduct business introduce new vulnerabilities alongside their incredible potential?
This is where the ongoing evolution of frameworks like the HITRUST CSF becomes paramount. It’s no longer just about having a strong defense; it’s about having an intelligent, adaptable defense system. This blog will explore why understanding the HITRUST CSF is more critical than ever, how it’s adapting to modern demand, and what this robust framework means for protecting sensitive data today and into the future. We’ll delve into its core components, the rigorous certification process, and how it stacks up against and integrates with other standards, all to give you a clearer picture of its vital role in today’s complex information security and risk management ecosystem.
Introduction to HITRUST CSF: More than Just a Framework
The HITRUST Alliance developed the HITRUST Common Security Framework (CSF) in 2007 to help healthcare organizations manage privacy, information security, and compliance more effectively. But it’s more than a static set of guidelines. The HITRUST CSF represents a modern, dynamic approach to security and risk management.
Definition and Purpose: Information Security and Risk Management
At its core, the HITRUST CSF integrates and harmonizes various standards and regulations, including HIPAA, NIST 800-53, ISO 27001 and 27002, PCI DSS, GDPR, and others, into a single, comprehensive set of controls. Its primary purpose is to provide organizations with a consistent and efficient approach to information security risk and compliance with diverse regulatory requirements.
The HITRUST CSF plays a crucial role in an organization’s broader information security and risk management strategy as well, serving as an active and operational framework rather than a passive checklist. It establishes a structured and systematic methodology for assessing vulnerabilities, evaluating potential threats, and implementing commensurate controls to mitigate identified risks. This methodical approach enables organizations to move beyond ad-hoc security measures towards a more cohesive and proactive stance. By guiding the implementation of specific security controls and processes, the CSF directly contributes to safeguarding the confidentiality, integrity, and availability of critical information assets. Consequently, the adoption and effective implementation of the HITRUST CSF allows an organization to build and demonstrate a robust, certifiable security posture.
Initially focused on the healthcare industry, which handles vast amounts of highly sensitive Protected Health Information (PHI), the CSF provides a tailored and robust pathway to address the stringent security and privacy requirements of HIPAA. This focus makes it an essential tool for healthcare providers, payers, and business associates striving to build trust and demonstrate due diligence in protecting patient data. However, the HITRUST Alliance points out that more recently, financial institutions, business service companies, and technology agencies are increasingly leveraging the framework to manage risk and meet diverse compliance obligations. Its comprehensive and adaptable nature makes it a valuable tool for any organization seeking to enhance its data protection practices.
Key Components of the Framework: A Structured Approach to Security
To achieve its objectives, the HITRUST CSF is built upon several key components that provide a comprehensive and structured approach to information security and privacy. The framework itself is methodically organized, encompassing 14 Control Categories, which are further divided into 19 Domains. Within these Domains lie 49 Control Objectives, supported by 156 Control References. The specific number of controls an organization must address can vary based on its unique risk profile and the CSF version being utilized.
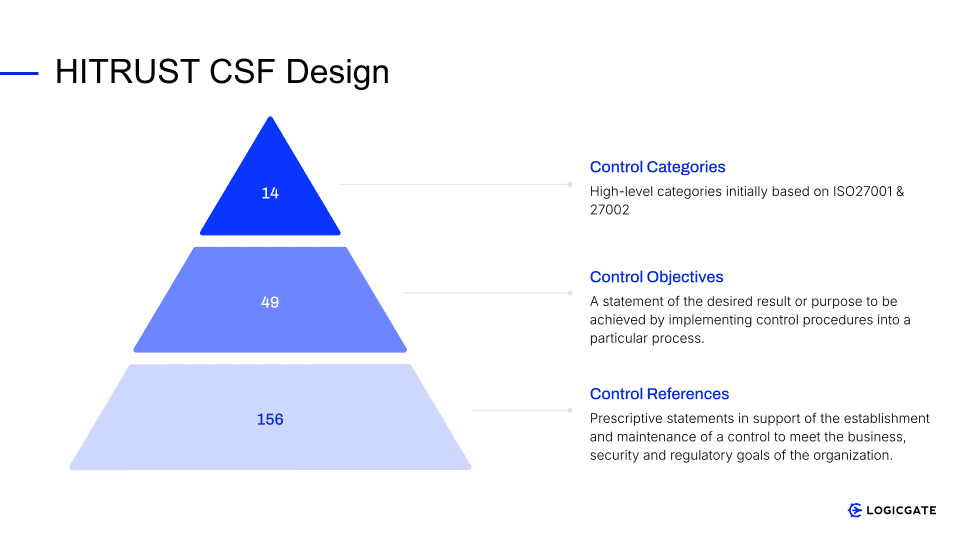
A fundamental component of the HITRUST CSF is its extensive library of security controls designed to ensure regulatory compliance across a wide array of requirements. These control references are prescriptive, offering specific guidance for organizations to implement effective security measures. They cover a broad spectrum of security domains, including access control, risk management, incident management, and business continuity, among others. This comprehensive set of control references allows the CSF to serve as a certifiable framework and enables organizations to demonstrate that their security programs meet the established standards.
One of the most significant strengths of the HITRUST CSF is its integration with numerous authoritative sources, including widely recognized regulations like HIPAA, standards from the National Institute of Standards and Technology (NIST), and requirements of the Payment Card Industry Data Security Standard (PCI DSS). This cross-mapping simplifies compliance efforts considerably and allows organizations to adopt a “assess once, comply many” strategy. Leveraging their HITRUST assessment, organizations can demonstrate compliance with multiple overlapping requirements and thereby reduce redundant efforts and improve efficiency.
Underpinning all aspects of the HITRUST CSF is a steadfast focus on safeguarding sensitive data. This includes, but is not limited to, Protected Health Information (PHI), Personally Identifiable Information (PII), financial data, and other forms of confidential or critical information. The framework provides detailed guidance and robust controls designed to protect these assets from unauthorized access, use, disclosure, alteration, or destruction, thereby helping organizations maintain the confidentiality, integrity, and availability of the sensitive information they manage.
HITRUST Certification: What It Means
Obtaining HITRUST certification is a significant undertaking and extends beyond a mere compliance initiative. It signifies that an organization has successfully implemented the HITRUST CSF controls to meet the rigorous, prescribed requirements of the selected assessment level. It’s evidence that the organization is demonstrating a high level of maturity in its security controls and privacy practices. The certification serves as a credible attestation to stakeholders, customers, and regulatory bodies of the organization’s verifiable commitment to protecting sensitive information and managing risk effectively.
An Overview of the Certification Process
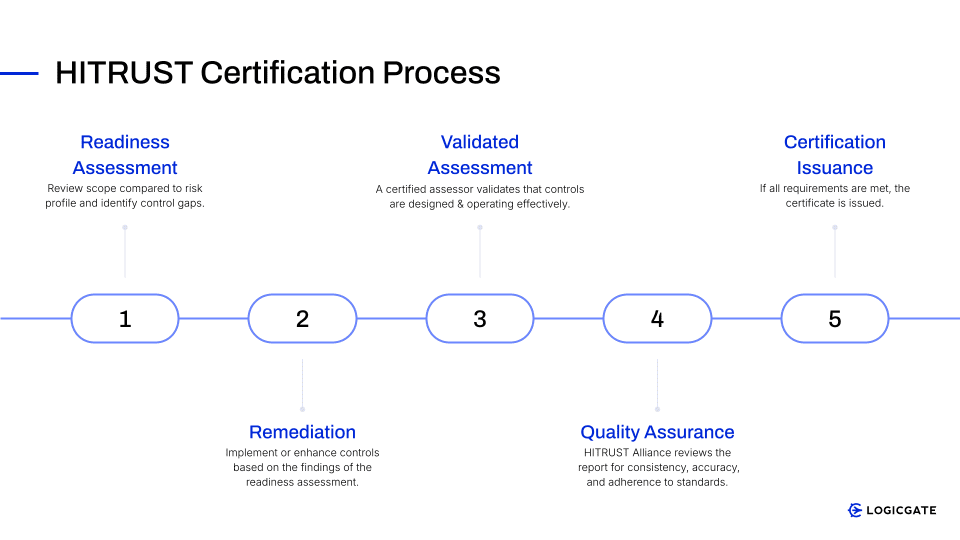
The path to HITRUST certification is a structured and demanding journey. The typical phases an organization will navigate are:
- Readiness Assessment: This preparatory phase allows an organization to scope the assessment based on its unique risk profile and identify potential gaps between its current control environment and HITRUST’s requirements.
- Remediation: Based on the findings of the readiness assessment, the organization undertakes remediation efforts. This involves implementing new security controls or enhancing existing ones to ensure they align with the CSF standards and address any identified deficiencies.
- Validated Assessment: An authorized HITRUST External Assessor, firm, or independent third party conducts a formal and meticulous validated assessment. The purpose is to validate that the organization’s controls are not only designed and documented appropriately but are also implemented and operating effectively over a sustained period. This phase includes thorough testing of controls, detailed review of documentation, and interviews with relevant personnel.
- HITRUST Quality Assurance Review: Following the validated assessment, the Assessor’s report is submitted to the HITRUST Alliance for a comprehensive quality assurance (QA) review. This QA process ensures consistency, accuracy, and adherence to the stringent standards set by HITRUST.
- Certification Issuance: Upon successful completion of the validated assessment and the subsequent QA review, if all requirements are met, the HITRUST Alliance issues the formal certification report.
Remember, the validated assessment, conducted by an independent, authorized External Assessor, is a critical component of the certification process. The External Assessor provides an objective evaluation of the organization’s controls against the CSF requirements. Their expertise is invaluable in navigating the complexities of the framework.
Tips for Becoming HITRUST Certified
Obtaining this valued certification requires diligence and a committed effort. To maximize your success, consider the following:
- Clearly defining the scope of the assessment tailored to the organization’s specific systems and risk factors.
- Utilizing the HITRUST MyCSF® portal for managing the assessment lifecycle, from readiness to validated assessments and corrective action plan management.
- Engaging a reputable and authorized HITRUST External Assessor firm to conduct the validated assessment.
- Undergoing rigorous, objective testing of the scoped controls to ensure they meet the CSF’s requirements.
- Systematically addressing any control deficiencies identified during the assessment process.
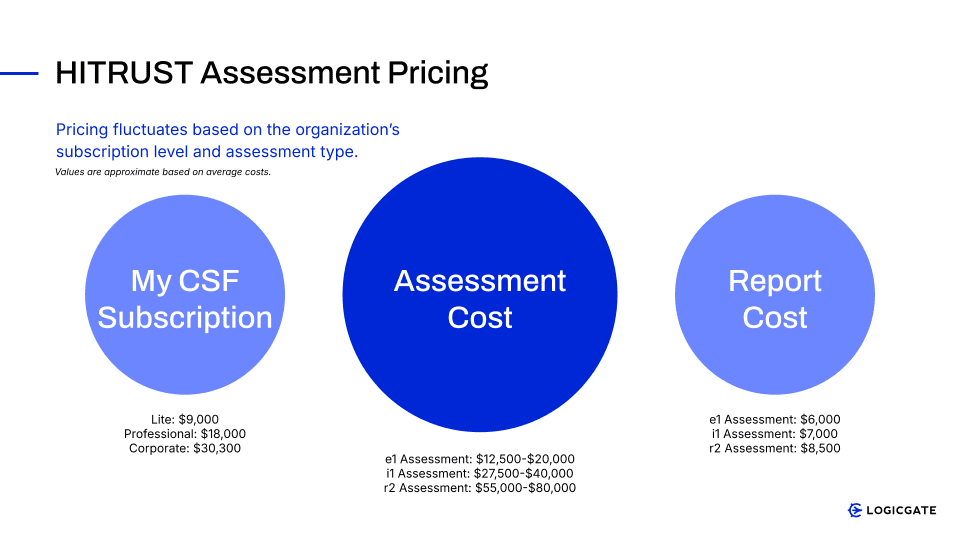
In addition, when planning for HITRUST certification, understanding the certification timeline and pricing is a key strategic consideration. The timeline can vary significantly, typically ranging from three to eighteen months. This duration is influenced by factors such as the chosen certification type (e1, i1, or r2), the organization’s size and complexity, its current security maturity, and the scope of the assessment. The associated pricing also fluctuates based on these elements, in addition to fees for the MyCSF tool subscription, the External Assessor’s services, and the HITRUST report cost. The total investment can range from approximately $17,000 to well over $100,000, necessitating careful budgeting and planning.
The Strategic Value of Being HITRUST Certified
Undertaking the rigorous process of HITRUST certification yields significant strategic benefits while reinforcing an organization’s commitment to security and compliance in a tangible way. First, the certification provides formal validation that an organization adheres to the exacting requirements of the HITRUST CSF for handling high-risk data. This proactively strengthens its defenses against the continuously evolving landscape of cyber threats and enhances its overall security posture and information protection.
Another key benefit is the streamlined approach to meeting regulatory requirements. The CSF’s comprehensive control mappings help organizations satisfy diverse compliance needs related to standards like HIPAA, NIST, and PCI DSS through a single, cohesive framework.
The HITRUST certification also serves as a powerful signal to customers, partners, regulators, and other stakeholders. It demonstrates a verifiable commitment to robust data protection and cybersecurity practices, thereby building trust and reinforcing relationships with service providers and clients alike. In many sectors, particularly healthcare and finance, HITRUST certification can also be a significant market differentiator. It may also contribute to more favorable terms for cybersecurity insurance.
By ensuring that relevant security controls are implemented and assessed efficiently, the framework helps organizations optimize their compliance programs and reduce the redundancy often associated with managing multiple, disparate compliance initiatives.
HITRUST CSF vs. ISO 27001: Key Differences
Both the HITRUST CSF and ISO 27001 are highly respected information security frameworks designed to help organizations protect sensitive information. Understanding their key differences is important for selecting the most suitable approach for an organization’s specific objectives and operational context.
Comparison of Frameworks
The primary difference between these frameworks comes from their respective prescriptiveness and scope. The HITRUST CSF is generally characterized by a more prescriptive and detailed control set. For example, an r2 certification involves assessment against a tailored selection of over 2,000 potential controls. Whereas the 2022 version of ISO 27001 specifies only 93 controls. Further, HITRUST provides specific implementation levels for each of its controls, while ISO27001 does not.
In addition, these frameworks embody distinct approaches to cybersecurity and risk assessment. ISO 27001 mandates a risk assessment process that allows organizations to identify and treat risks according to their own defined methodology and risk appetite. The HITRUST CSF provides a more structured and prescriptive risk and control-based methodology, where control requirements are determined by a combination of inherent risk factors and CSF-defined levels.
While the HITRUST CSF originated with a sector-specific focus on U.S. healthcare organizations, it has evolved to become broadly industry-agnostic and is used across various sectors. In contrast, ISO 27001 is an international standard for general information security management, applicable to any organization, regardless of its sector, size, or geographical location. The optimal framework choice will depend on an organization’s unique requirements, industry context, regulatory environment, customer demands, and overall strategic objectives.
Integration with Other Standards
Beyond ISO 27001, the HITRUST CSF strategically incorporates and maps to fundamental elements from other established frameworks, such as NIST 800-53. Consequently, by achieving HITRUST certification, an organization can often concurrently demonstrate that it addresses many of the core requirements embedded within these other standards, providing a unified approach to multifaceted compliance.
This consolidated method also serves as an effective mechanism for streamlining compliance requirements across industries. It helps organizations reduce the complexity and redundancy often encountered when managing numerous, frequently overlapping, security and privacy mandates from different regulatory bodies or industry standards. This “assess once, comply many” capability can translate into tangible efficiencies in terms of both time and resource allocation for compliance programs.
Navigating the HITRUST Assessment Process: A Roadmap to Certification
Successfully navigating the HITRUST Assessment Process requires a clear understanding of the available assessment types, their specific requirements, and the overall methodological journey involved in achieving certification.
Understanding the Types of Assessments
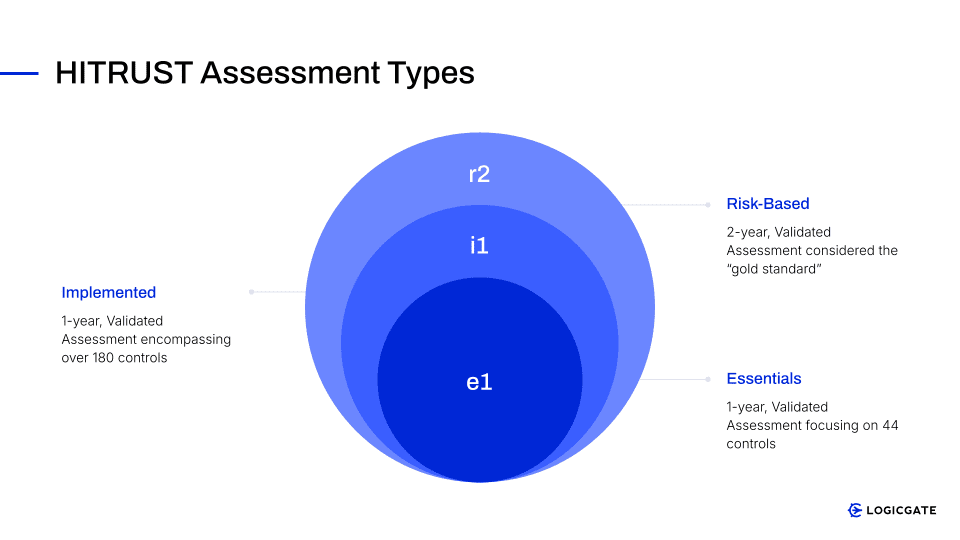
The e1 assessment is a 1-year validated assessment that focuses on 44 foundational cybersecurity controls. The e1 assessment serves as an accessible entry point for organizations with limited risk profiles or those initiating their formal compliance programs seeking a baseline level of assurance. It is designed for efficiency and can often be completed within a relatively short timeframe.
The i1 assessment is a more comprehensive, threat-adaptive, validated assessment, encompassing over 180 controls, including the 44 from the e1 assessment. It provides a moderate, yet robust, level of assurance suitable for organizations with established security programs needing to demonstrate good security hygiene and active threat preparedness. The requirements for the i1 assessment are regularly updated by HITRUST to address emerging cyber threats.
Lastly, the risk-based, validated r2 assessment offers the highest level of assurance. The r2 is the most comprehensive assessment and is often referred to as the “gold standard” of HITRUST certification. The number of controls is dynamic, averaging approximately 385 out of over 2,000 possible controls in the CSF. The r2 assessment is tailored based on an organization’s specific risk factors, size, system complexity, and regulatory landscape. It is valid for two years, with an interim assessment required after one year to ensure continued adherence.
Irrespective of the chosen assessment type, the HITRUST MyCSF® platform helps organizations manage all stages of the HITRUST process, from scoping and initial self-assessment activities through managing validated assessments, storing evidence, and tracking corrective action plans. Conducting a self-assessment in the MyCSF® tool allows an organization to gauge its readiness and identify gaps before a formal, validated assessment. While valuable, it does not replace the need for a third-party validated assessment conducted by an authorized HITRUST External Assessor, which is required for certification.
Addressing Risk Factors and Remediation
The HITRUST CSF is inherently risk-based in its design and application. The assessment process is structured to assist organizations in identifying and addressing risk factors by systematically examining various organizational, technical, and regulatory considerations that influence their specific control environment. Once these risks and any associated control deficiencies are identified, the subsequent step involves developing and implementing robust remediation plans. This process is not merely about fixing isolated problems, but strategically strengthening the organization’s overall security posture and enhancing its demonstrable resilience against identified risks.
A core tenet of the HITRUST methodology is identifying and managing information risk in a structured manner. The framework provides a well-defined and systematic approach for evaluating vulnerabilities and potential threats specific to an organization’s environment. This enables organizations to make informed, prioritized decisions regarding the implementation and continuous improvement of appropriate and effective security controls tailored to their risk landscape.
In addition, the HITRUST CSF directly incorporates controls pertinent to critical areas such as information security, incident management, and business continuity planning. It guides organizations in developing strategies to not only prepare for and respond effectively when cyber threats materialize, but to also ensureoperational resilience and capacity to recover core functions from significant disruptions.
Final Thoughts on HITRUST Compliance: A Commitment to Continuous Improvement
Successfully achieving HITRUST certification is a testament to an organization’s dedication to implementing and upholding robust security and privacy practices. However, maintaining compliance is an ongoing imperative. This requires a sustained commitment to continuously monitoring the effectiveness of controls, proactively adapting to new and evolving threats, and diligently staying informed about updates within the HITRUST CSF itself, as well as shifts in the broader regulatory and cyber threat landscapes.
Achieving and Maintaining Compliance
At its core, the HITRUST CSF promotes and facilitates a dynamic risk management methodology that inherently cultivates a culture of continuous improvement within an organization. The iterative cycle of performing regular risk assessments, validating control effectiveness, implementing remediation plans, and proactively updating security practices is essential for maintaining a strong and resilient security posture. This disciplined process is about the progressive enhancement and maturation of an organization’s protective capabilities over time.
Given the dynamic and persistent nature of cyber threats, coupled with the continuous evolution of global privacy regulations, an organization’s security and privacy controls must not be viewed as static implementations. They necessitate regular review, timely updates based on new risks or requirements, and thorough testing to ensure their sustained effectiveness in protecting sensitive information. This ongoing diligence and adaptation form the bedrock of resilient and trustworthy data protection practices.
Future Trends in HITRUST CSF: Anticipating an Evolving Landscape
The HITRUST CSF is a forward-looking framework, intentionally designed by the HITRUST Alliance to evolve and anticipate future trends in the cybersecurity and data protection domains. HITRUST is committed to the continual refinement and updating of the CSF. Organizations can expect ongoing adaptations to emerging cybersecurity frameworks, ensuring alignment with new threat vectors, significant technological advancements, and other influential standards like the NIST Cybersecurity Framework 2.0 and international privacy benchmarks.
In addition, while its origins are deeply rooted in the U.S. healthcare sector, the adoption of the HITRUST CSF continues to gain considerable momentum globally, demonstrating its expanding relevance beyond the healthcare sector. This trend underscores its growing recognition as a versatile and trustworthy benchmark for comprehensive security and privacy assurance.
Future iterations of the HITRUST CSF will likely incorporate more specific and nuanced guidance and controls related to the unique security and privacy challenges and opportunities presented by rapidly advancing technologies like artificial intelligence (AI) and machine learning (ML), the Internet of Things (IoT), and potentially the long-term implications of quantum computing. HITRUST has already taken steps in this direction by introducing an AI Security Certification and an AI Risk Management Assessment.
Lastly, another continuing trend is the pursuit of greater efficiency and effectiveness within the assessment process itself. This may include further advancements in automation for evidence collection and validation, as well as evolving models for shared responsibility in cloud environments and third-party risk management. This has the potential to lead to more dynamic or near-real-time continuous assessment paradigms.
Conclusion: A Framework for Modern Data Protection Excellence
In an environment where data is an exceptionally valuable organizational asset and digital threats represent an ever-present and evolving concern, the HITRUST CSF distinguishes itself as a robust, adaptable, and comprehensive framework. It provides organizations with a clear, credible, and structured pathway to safeguarding sensitive information and effectively managing the multifaceted complexities of regulatory compliance. While the journey to achieve and maintain HITRUST certification requires significant dedication, strategic planning, and resource investment, the resulting benefits are substantial and strategically vital.
As the digital landscape continues to present both unprecedented opportunities and sophisticated new risks, frameworks like the HITRUST CSF, particularly when supported and operationalized through the capabilities of advanced Governance, Risk, and Compliance (GRC) platforms such as LogicGate Risk Cloud, will play an increasingly crucial and indispensable role. They represent the methodologies, standards, and tools that empower organizations not merely to react to threats, but to proactively build, maintain, and continually improve a resilient and secure operational environment in the face of modern information security and privacy challenges.
Is your organization prepared to elevate its approach to HITRUST compliance and fortify its data protection strategies? Explore how LogicGate Risk Cloud can support your journey to certification and assist in the establishment of a resilient, intelligent, and adaptable defense system. We invite you to request a demo to learn more about streamlining your path to HITRUST compliance and leverage our first-to-market value realization application to demonstrate tangible ROI. Book a demo today!

