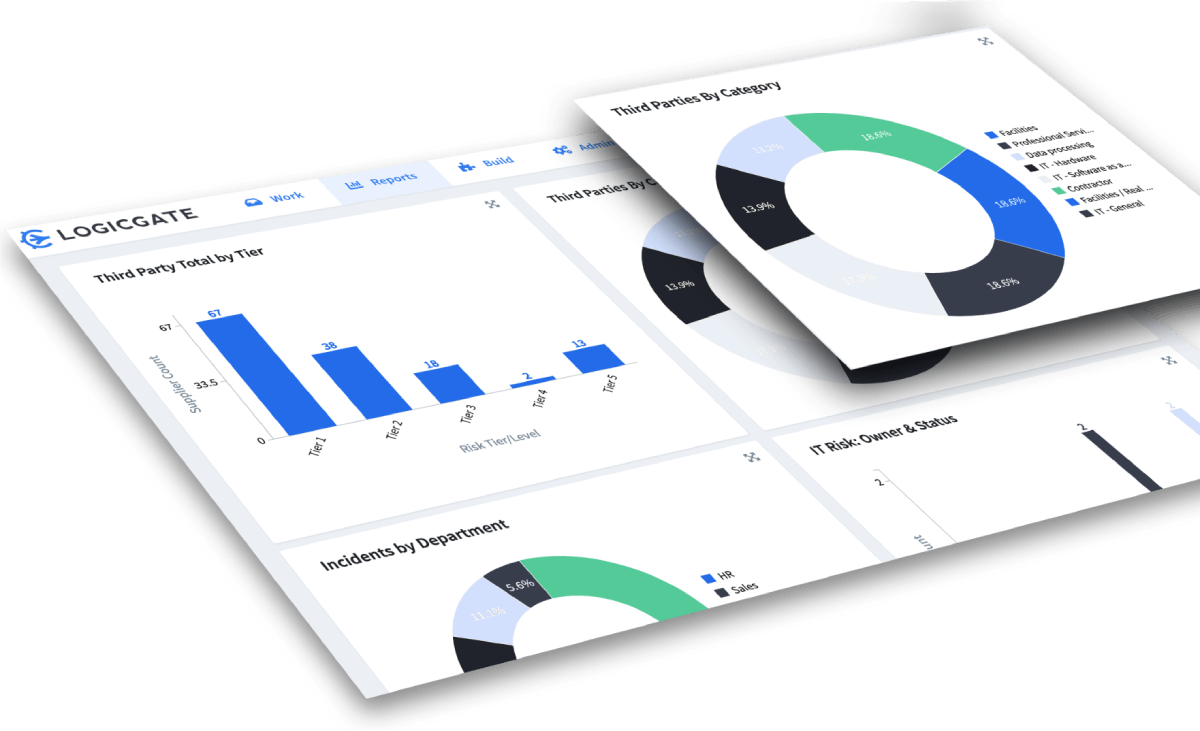
IT Security Risk Management Software
LogicGate is a powerful Security Risk Management software that transforms how enterprises operate their cybersecurity risk programs. Capture, analyze, and reduce information risk with full transparency and control.