A Look Back at LogicGate’s 2024 Annual Agility User Conference
In March we hosted our annual Agility User Conference in Chicago gathering hundreds of Compliance, Cybersecurity and Risk…
Every login to every digital tool your organization uses, and every manufacturer you rely on for materials. Every email or direct message sent to a contractor or consultant. Every credential left forgotten and unrevoked once your business with those entities has concluded. Every single connection point between your organization and a third-party service provider or vendor represents an opportunity for risk and bad actors to enter your organization.
Those connections have only grown in number and complexity in our digital-first landscape. That’s why organizations that commit to staying on top of third-party risk assessment have a competitive advantage when it comes to data security.
No two vendors are the same, and each carries different levels of risk. So where to begin? This article provides a comprehensive game plan for building an effective program to assess and mitigate third-party risk.
Third-party risk refers to any risk that enters your organization because of your relationships with contractors, consultants, service providers, or other types of vendors that your organization works with in the course of routine business operations.
That public relations agency with early access to sensitive information about big announcements? That’s third-party risk. The provider of your cloud-based security solution? The one with access to significant portions of your network? Definitely third-party risk. Even the company you contract with to clean your offices each night can introduce third-party risk to your organization.
Let’s explore some specific types of third-party risk.
This type of third-party risk is probably the most visible in most organizations. It’s the risk that a threat actor will manage to work their way into your systems via a third-party’s access to your network or as a result of improper employee use of a cloud-based software platform.
Though technology has allowed organizations to push innovation and productivity to previously unseen levels, it has also introduced significant amounts of risk. Retail giant Target, for instance, was famously victimized by a data breach that originated with their HVAC contractor's access to their point-of-sale system, illustrating the consequences of how a simple oversight can cause a big problem.
Aside from the talent in its workforce, data is arguably the most valuable asset a company possesses these days, and the volume of data created each day is growing exponentially. Much of this data is personally identifiable information, intellectual property data, financial data, or critical infrastructure information — both types of data that can cause big problems if it falls into the wrong hands.
Every organization relies on supply chains at some point, and any point at which they break down can cause headaches — or worse — up and downstream. Supply chain risk is the risk that one or more of your suppliers will become compromised, leading to a cyber incident, or disrupted, leading to delays and lost revenue.
The infamous NotPetya cyberattack and the outbreak of the COVID-19 pandemic are great examples of supply chain risk events that materialized and crippled worldwide shipping, a crucial component of most supply chains.
Any partnership with a third-party contractor, consultant, vendor, or personality carries the risk that one or both of you will become embroiled in a controversy, fall victim to a major cyberattack, or experience some other event that tarnishes each of your brand’s reputations by association.
Last year’s dispute between apparel giant Adidas and Kanye West is an example of this type of risk. Though Adidas’s partnership with West’s Yeezy apparel brand was initiated prior to a series of highly controversial public statements by the rapper, the company swiftly terminated the deal to distance itself from him amid the fallout from his actions. Afterward, the company faced lost revenue and a lawsuit by investors.
On the flip side, this type of risk can occasionally lead to strategic advantage. Following Colin Kaepernick’s public protest of systemic racism during NFL games, Nike — no stranger to taking stands and courting controversy — initiated a marketing partnership with the former quarterback. The result? A boom in sales.
This is the risk that third parties you work with will fail to comply with regulatory requirements, causing negative consequences for your organization. If one of your contractors is violating labor or environmental laws, you could easily find yourself in regulators’ crosshairs and financially on the hook when the penalties start to roll in.
While you might be testing the effectiveness of your processes, controls, and policies regularly to ensure they’re working, you need to be sure that the third parties you work with are meeting the same standards. An operational failure at one of your vendors can easily spill over into an operational failure for your organization.
When you execute a contract with a vendor, the expectation is that you’ll get the services or goods that you paid for, right? That may not be the case if your chosen contractor is in poor financial health: It could go out of business and leave you high and dry, interrupting your operations, and damaging your revenue. Plus, you likely sent a lot of sensitive information and data to that company.
That’s what happened to Silicon Valley Bank in March 2023. Numerous startups and venture funds trusted SVB to keep their deposits safe, but poor risk management and bad investments by the bank ended up seeing it fail, leaving all of those customers wondering if they’d be able to get their money out and make payroll the following week.
Any of the above scenarios has the potential to cause anything from a minor headache to catastrophic, irreparable damage to your organization. Failing to adequately manage third-party risk essentially means you’re flying blind, giving contractors and vendors access to your organization and its assets without considering the various risks associated with them — and that can carry serious consequences, financial or otherwise.
Here are a few recent examples of third-party risk causing major problems for organizations:
In each of those scenarios, the victims suffered significant financial and reputational damage.
We’ve established all of the very important reasons why every organization needs to stay on top of third-party risk. Now let’s get into how to go about doing that.
The process of evaluating third-party risk so that it can be mitigated is known as third-party risk assessment. When properly designed and executed, these assessments are designed to make sure your organization has a pulse on the security posture, health, and compliance practices of each and every vendor it works with.
The first step in carrying out a vendor risk assessment is to figure out which risks your organization is exposed to through its vendor ecosystem.
A good way to go about doing this is to make a list of all the different adverse events that your organization could potentially face based on stakeholder and subject matter expert interviews, data analyses, review of external media, and other sources of information. This list is known as a risk register.
You should also use risk quantification methods to tie each of those risks to the potential impact it could have on your organization, financial or otherwise.
With your risk register in hand, begin categorizing each risk based on the types of third-party risk detailed above or others that are relevant to your organization.
Next, you’ll want to begin mapping each of your risks to each of your vendors to develop risk profiles. These profiles will paint a picture of all the different types of risk a single vendor could introduce to your organization, and allow you to group vendors together based on similarities in their risk profiles.
Pro tip: It can be helpful to visualize your vendor risk profiles, so you can see where they connect to each part of your organization, and to each other.
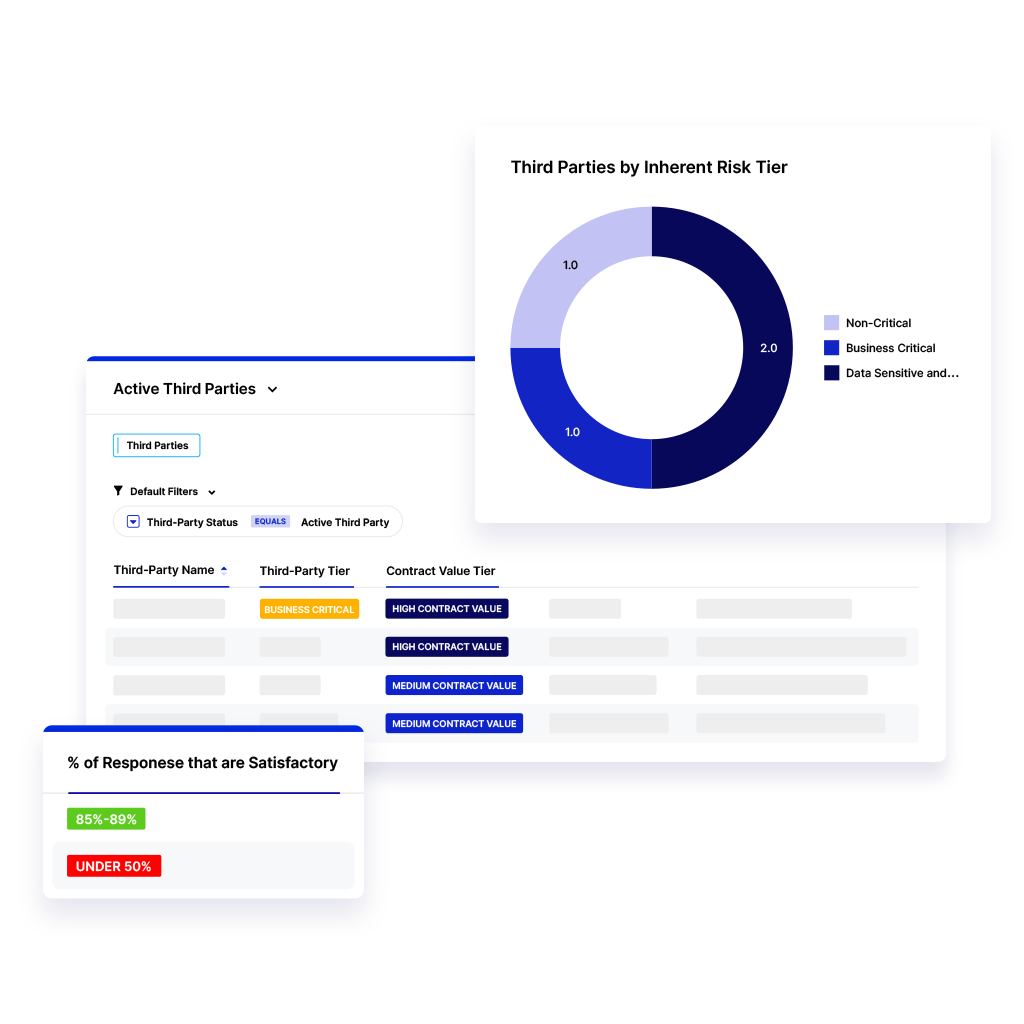
Since some risks are much more of a threat to your business than others, it makes sense to bucket your vendors into tiers based on the potential total severity of the risks associated with them.
That catering company that delivers boxed lunches to your office’s front desk for an executive meeting and then leaves? It’s probably safe to place them in your “low” risk bucket. But the cybersecurity contractor with access to almost every corner of your network? That one belongs in the “high” or “critical” risk bucket.

Putting this work in will help you focus your third-party and vendor risk assessment and mitigation efforts on the relationships that have the highest potential to cause problems first.
Now that you know which risks are associated with which vendors and you’ve determined which of those vendors carry the most risk, it’s time to evaluate their security practices to make sure they’re adhering to the appropriate processes and standards to keep the data and assets you allow them to access secure.
You’ll want to quiz each of your existing vendors on their security practices and make them prove that they’re compliant with any risk management and security frameworks you deem necessary, including SOC 2, NIST, SIG Lite, ISO 27001, and others, and examine their financial health to make sure they’re stable and will be a reliable partner.
A caveat: It’s often easier to obtain this type of information from large, public companies than smaller, privately-held organizations. You’ll need to work more closely with those vendors to obtain equivalent information that offers the level of assurance you require.
You’ll also want to look at things like the vendor’s geographic location and reputation. Are they located in a volatile country or region where conflicts or unrest could potentially disrupt their operations — and, by association, your own operations — or are they based out of a country that’s targeted by international sanctions, like Russia or North Korea? Check out any media coverage of a prospective vendor, too. Have they ever been at the center of a big controversy? Are they the target of a major lawsuit?
Because some vendors carry less risk than others, it’s a good idea to develop a number of different third-party risk assessment questionnaires. That way, you can send shorter, simpler questionnaires to less risky partners to streamline their assessment and speed things up, while vendors that carry critical risk will receive much more intricate and comprehensive questionnaires. That said, the more comprehensive you are, the less risk will make it into your organization overall.
Ultimately, once you’ve assessed each of your third parties and vendors, you’ve got a big decision to make: How game-changing is the technology or service the vendor is offering, and are you willing to assume the risk that comes along with it for the benefits? Remember, no vendor is perfect. If you do decide to work with a particular vendor despite the risks, be sure that you’ve put appropriate controls and processes in place to mitigate them.
Once you’ve assessed your existing third-party relationships, you can adapt these questionnaires for use in new vendor onboarding. You can also repurpose them for vendor offboarding, an equally important part of the vendor lifecycle, since that’s when you’ll revoke the privileged access a third party has to your system.
If you do decide to move forward with a vendor following your assessment, you’ll need to decide how to handle each of the risks they’ll bring along with them. You can:
Third-party risk assessment is never a “one-and-done” activity. Every organization’s security posture and risk and compliance landscapes are constantly changing, and it’s crucial that your organization has a system in place for re-assessing each vendor relationship on a regular basis. You should also design key performance and risk indicators to gauge the success of your third-party risk management and mitigation program, so you’ll know what’s working and what needs to be improved.
Many organizations rely on a patchwork of spreadsheets and other disjointed documentation to keep track of their third-party risk assessments and vendor risk, but that’s a very difficult system to scale. And with the sheer number of vendor relationships most modern organizations have, scale is the name of the game.
A modern GRC platform, like LogicGate Risk Cloud®, can help here. These systems allow you to connect, centralize, and automate all of your third-party risk management controls, audits, and due diligence in one place. That allows you to automate repetitive tasks, reduce human error, and speed up vendor onboarding.
So, what goes into a third-party risk assessment questionnaire? Every question about every risk, policy, process, and control that the vendor may have or be subject to, to the extent necessary by the risk category they fall into.
Here are some of the most important things you’ll want to make sure you ask about:
Here, you’ll want to make sure you’re asking the right questions to determine whether a vendor is aligned with your organization on cybersecurity standards, controls, training programs, and framework compliance. You’ll also want to ensure that the software tools that they’re using to run their own day-to-day operations are secure. The risks associated with those relationships are known as fourth-party risk. Yeah, this can get pretty exponential.
Some questions to ask:
When assessing third-party cybersecurity risk or if your organization is being assessed for cybersecurity risk by a potential customer, it can be helpful to create a software bill of materials, or SBOM.
An SBOM is a nested list of all of the different software components that underlie your own product or the one you’re about to implement for your organization, so that you or your potential client can quickly assess any security risks associated with them. Having a SBOM prepared or asking your vendors to provide them can speed up the third-party risk assessment process.
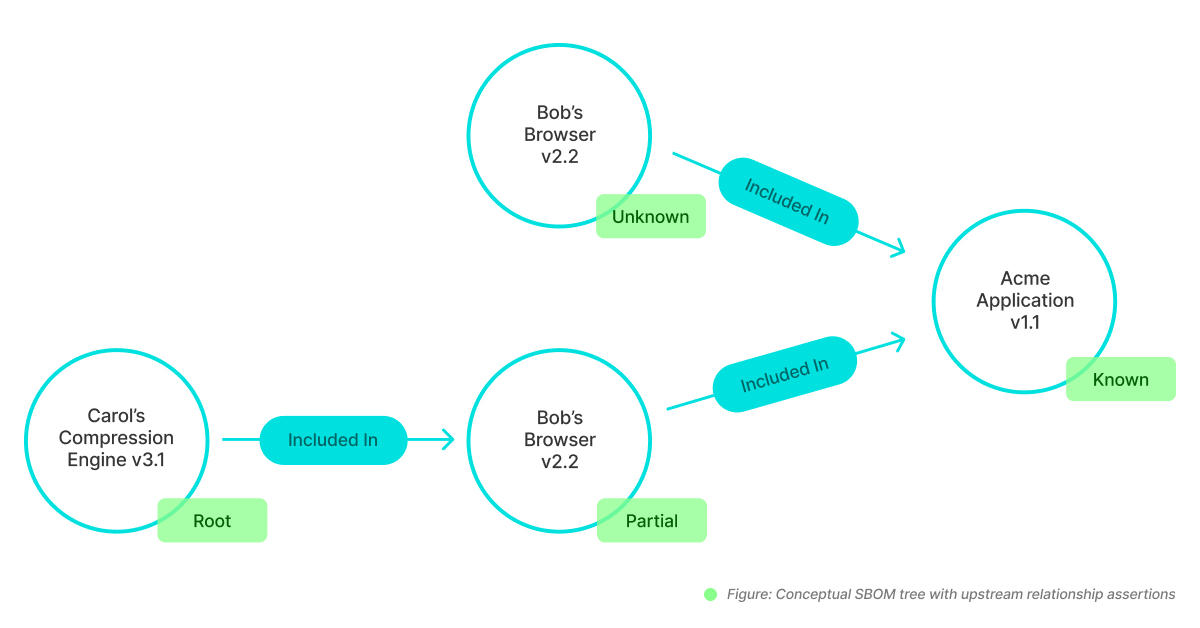
Source: National Telecommunications and Information Administration
For public companies, much of this information can be gleaned from mandatory filings like 10Qs and 10Ks. When it comes to private companies, it may come down to asking them to show you bank statements or balance sheets.
Ask to see copies of any audits, internal or external, to make sure the vendor is fully compliant with all applicable legal and regulatory requirements.
If you’re being assessed: It’s a good idea to compile as much of this information as possible into a prepared “trust package” that can be handed off to the client at the start of the third-party risk assessment process. Any more specific questions can be answered afterward.
Managing third party risk is a marathon, not a sprint. You can make sure your organization keeps pace by following the above framework and powering it all with the right GRC technology.LogicGate Risk Cloud’s Third-Party Risk Management Solution can help you efficiently assess third-party risks, implement strategies to improve your risk posture, and onboard vendors faster. Schedule a demo today.
SOC 1®, SOC 2® and SOC 3® are registered trademarks of the American Institute of Certified Public Accountants in the United States. The AICPA Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy is copyrighted by the Association of International Certified Professional Accountants. All rights reserved.
In March we hosted our annual Agility User Conference in Chicago gathering hundreds of Compliance, Cybersecurity and Risk…
As a GRC software company founded by practitioners for practitioners, we understand your GRC program needs more than…
To be the best company, we need the best people. The employees of LogicGate are our most valuable…
